TryHackMe: Anthem
This box is really easy, it doesn’t really any exploitation, just enumeration, but it is a Windows machine…
Scanning
Looking for open ports, and service information:
crazyeights@es-base:~$ nmap -Pn --script=banner --min-rate 200 -T4 --min-parallelism 100 10.10.142.92
Starting Nmap 7.80 ( https://nmap.org ) at 2021-01-13 11:06 EST
Nmap scan report for 10.10.142.92
Host is up (0.13s latency).
Not shown: 998 filtered ports
PORT STATE SERVICE
80/tcp open http
3389/tcp open ms-wbt-server
Web
Index Page:
Enumeration:
Enumeration can mostly be done manually.
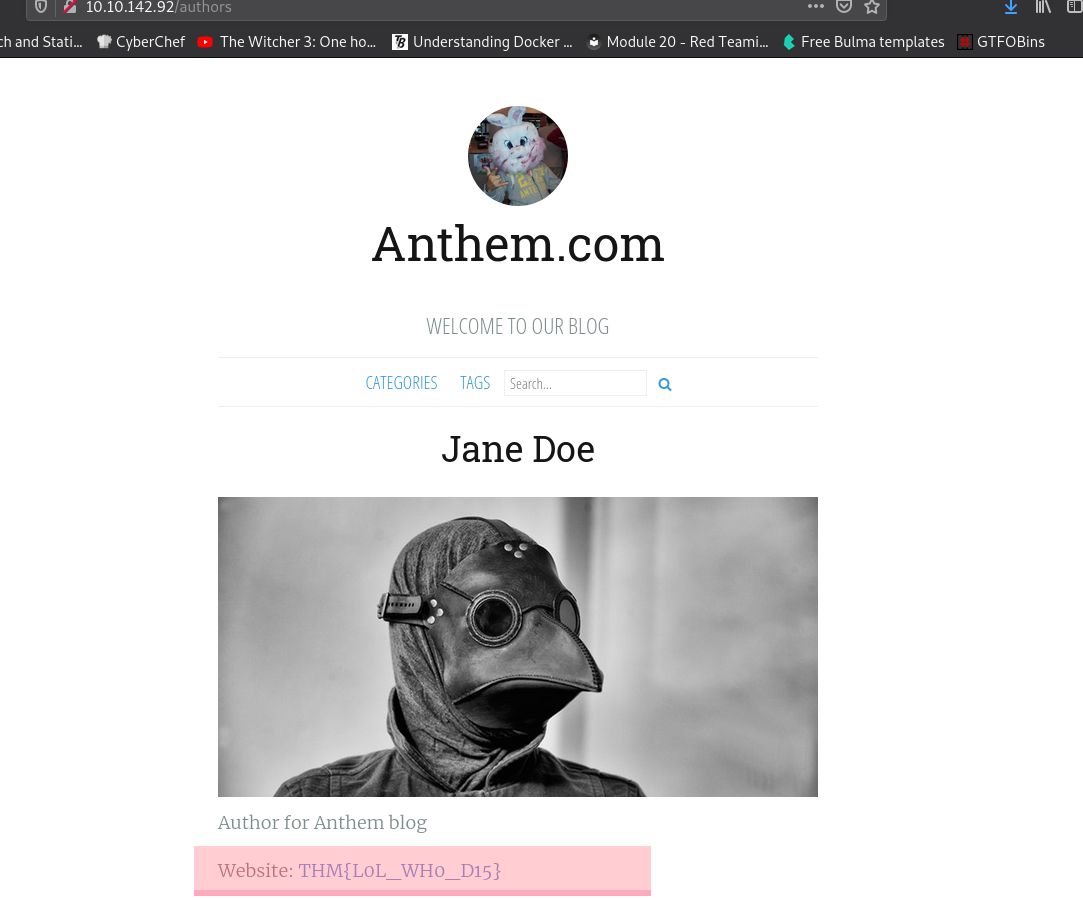
We find a user Jane:
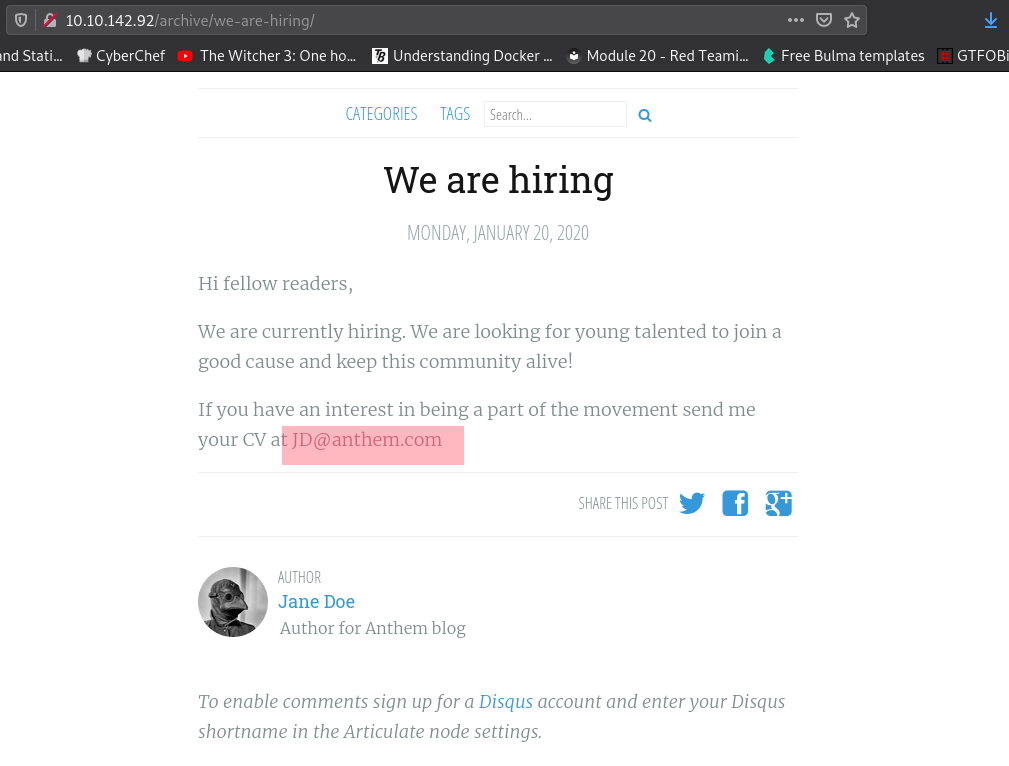
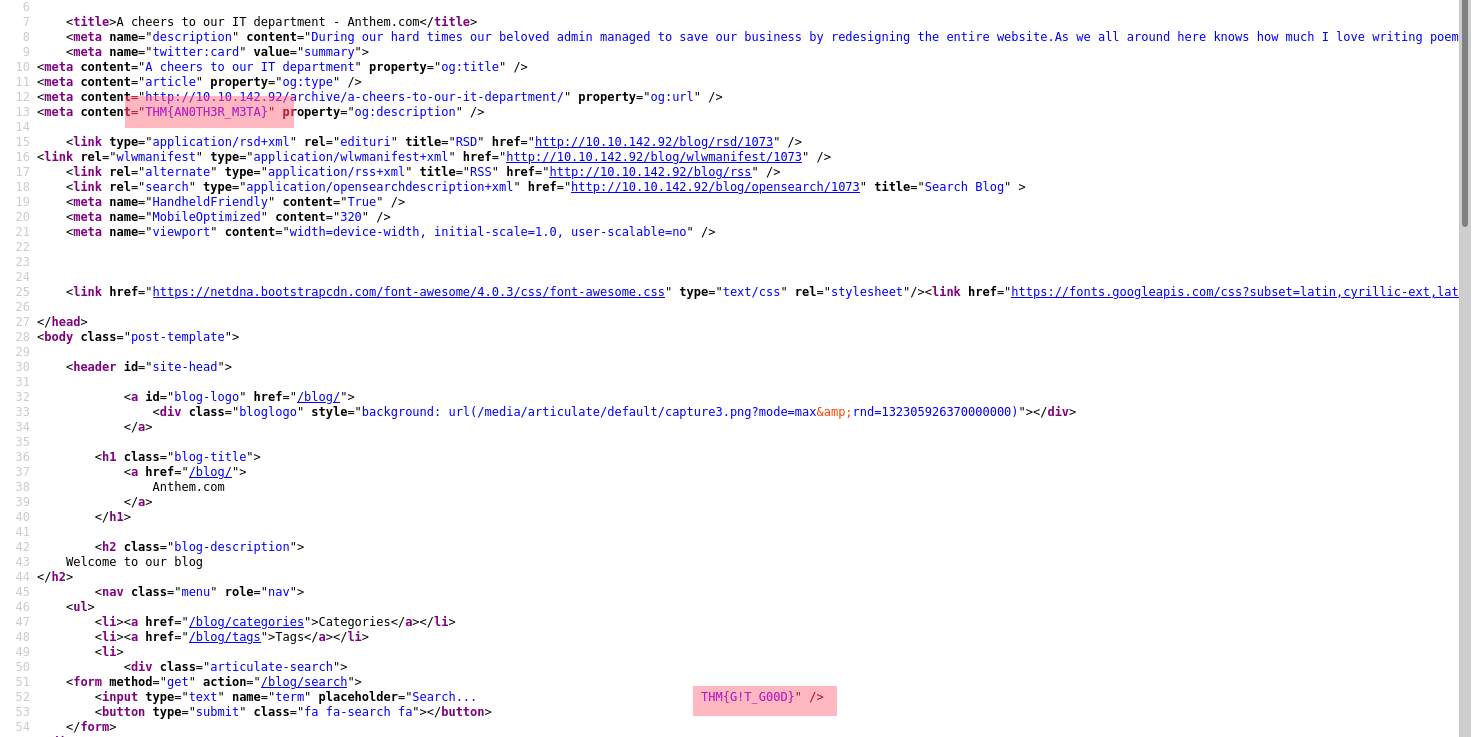
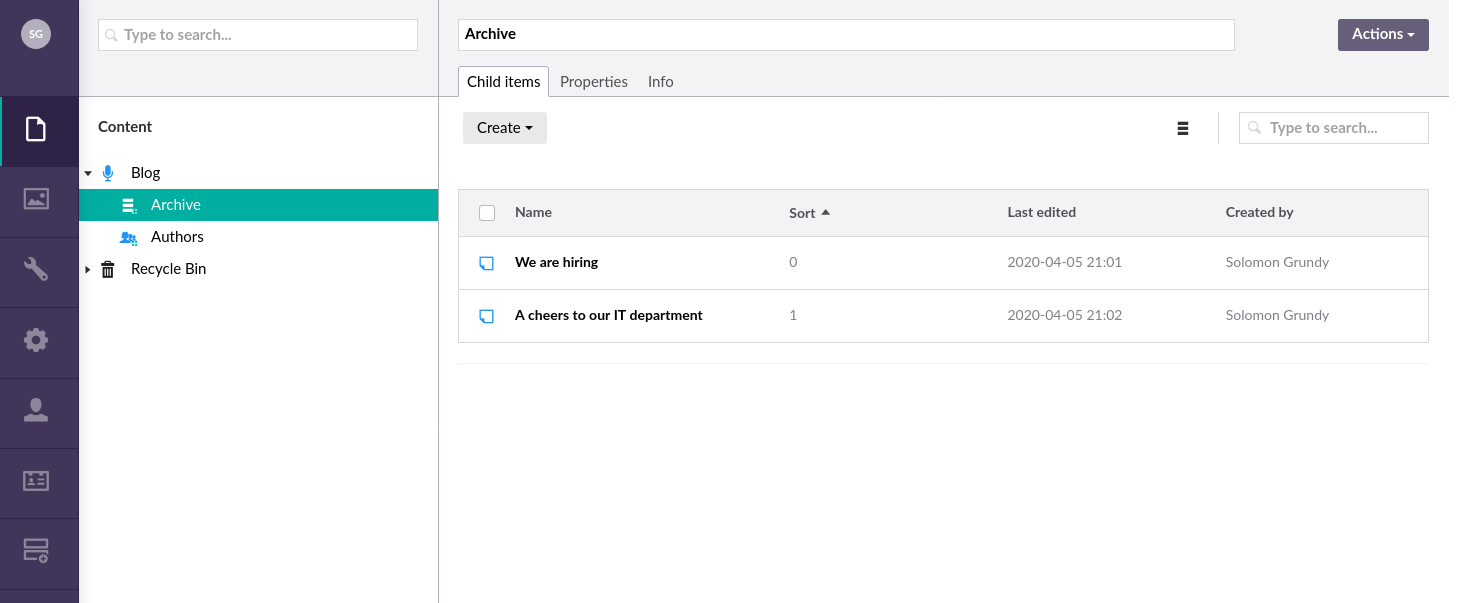
There is also a cryptic message in the post “A cheers to out IT department” about the administrator.
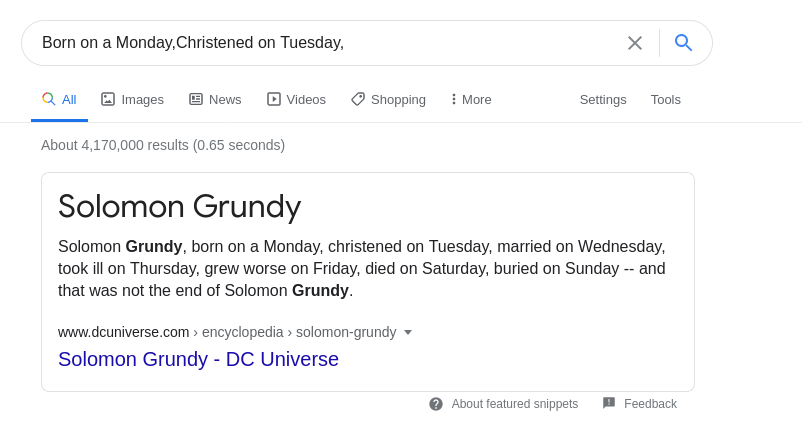
Looking it up we get a username:
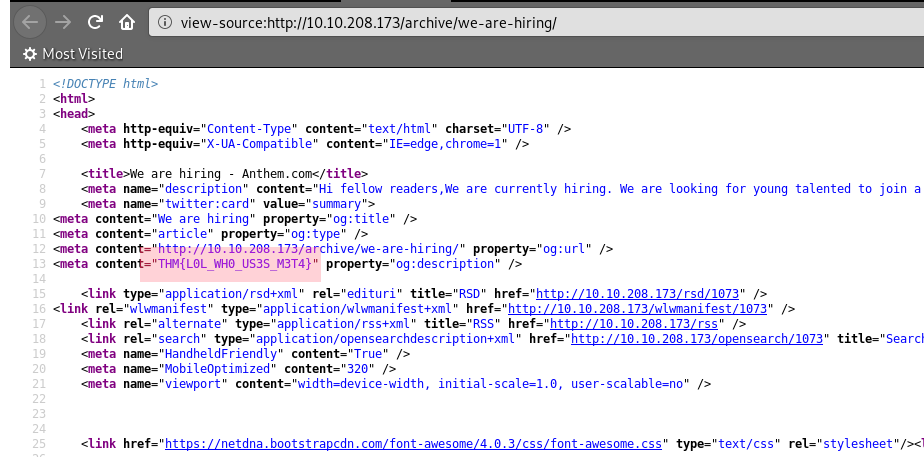
There is four flags to find, we can find them manually just by poking around:
Using nikto to enumerate:
We check robots.txt:
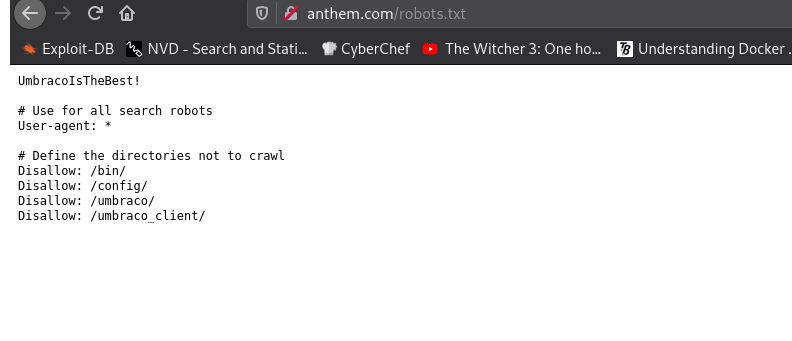
UmbracoIsTheBest! is the password for the user Solomon Grundy.
Umbraco:
Go to /umbraco to access Umbraco CMS
Solomon Grundy’s username follows the same format as Jane Doe’s, that being [First Initial][Last Initial]@anthem.com
Credentials: SG@anthem.com:UmbracoIsTheBest!
You can log in and look around but there is no additional info.
Remote Desktop:
Use the umbraco password:
crazyeights@es-base:~$ rdesktop 10.10.142.92:3389 -u SG -p UmbracoIsTheBest!
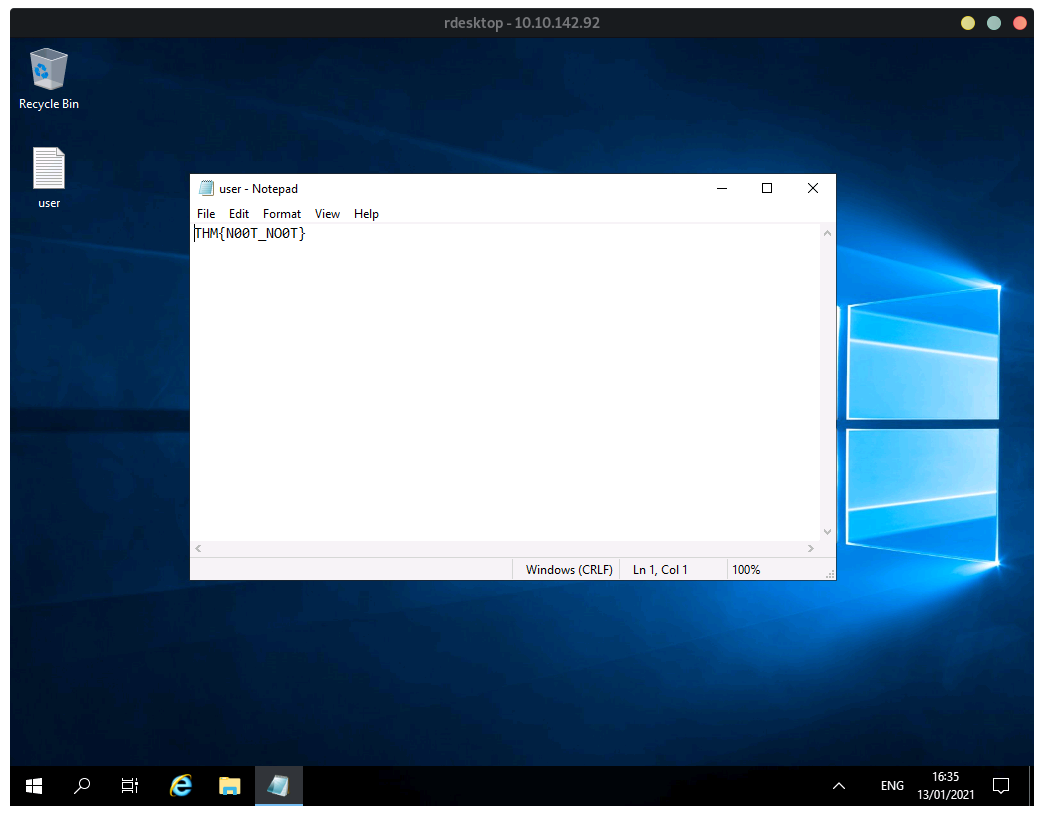
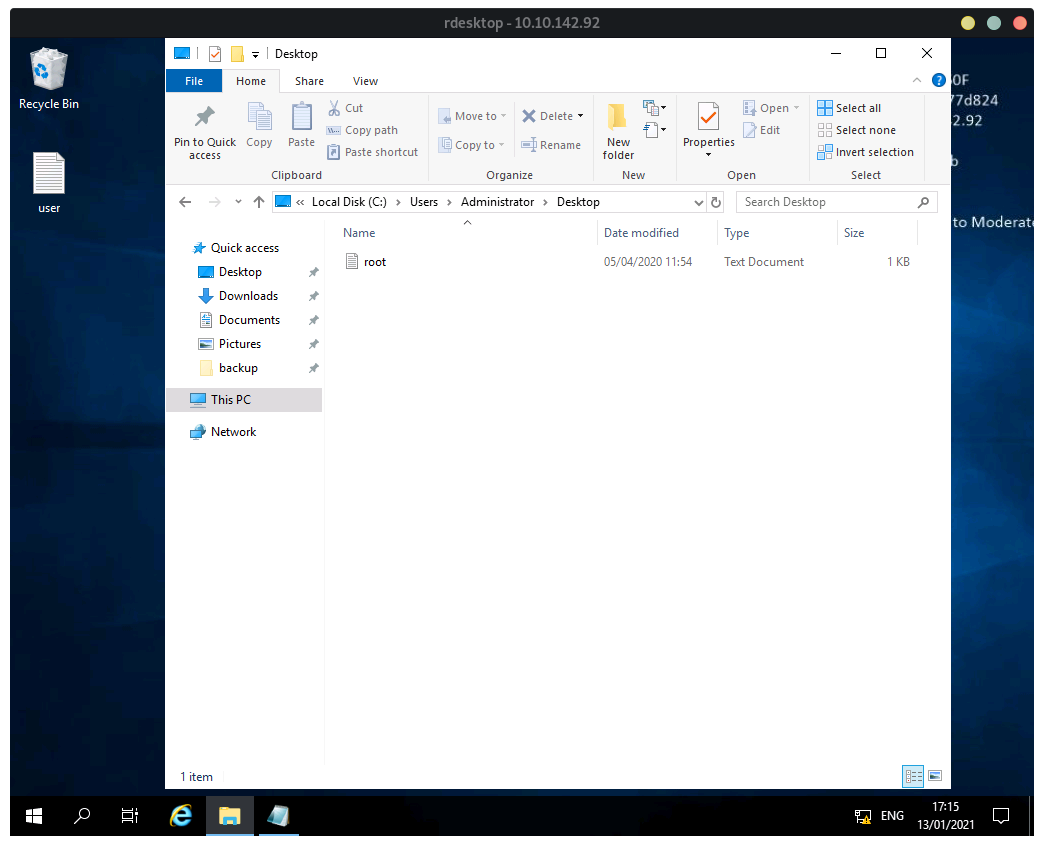
User Flag:
The user flag can be found on Desktop:
The next step is to find the Administrator’s password
When we enable Hidden Files we see folder backup containing the file restore.
We do not have permissions to access restore, but we can modify the permissions to allow ourselves to access it:
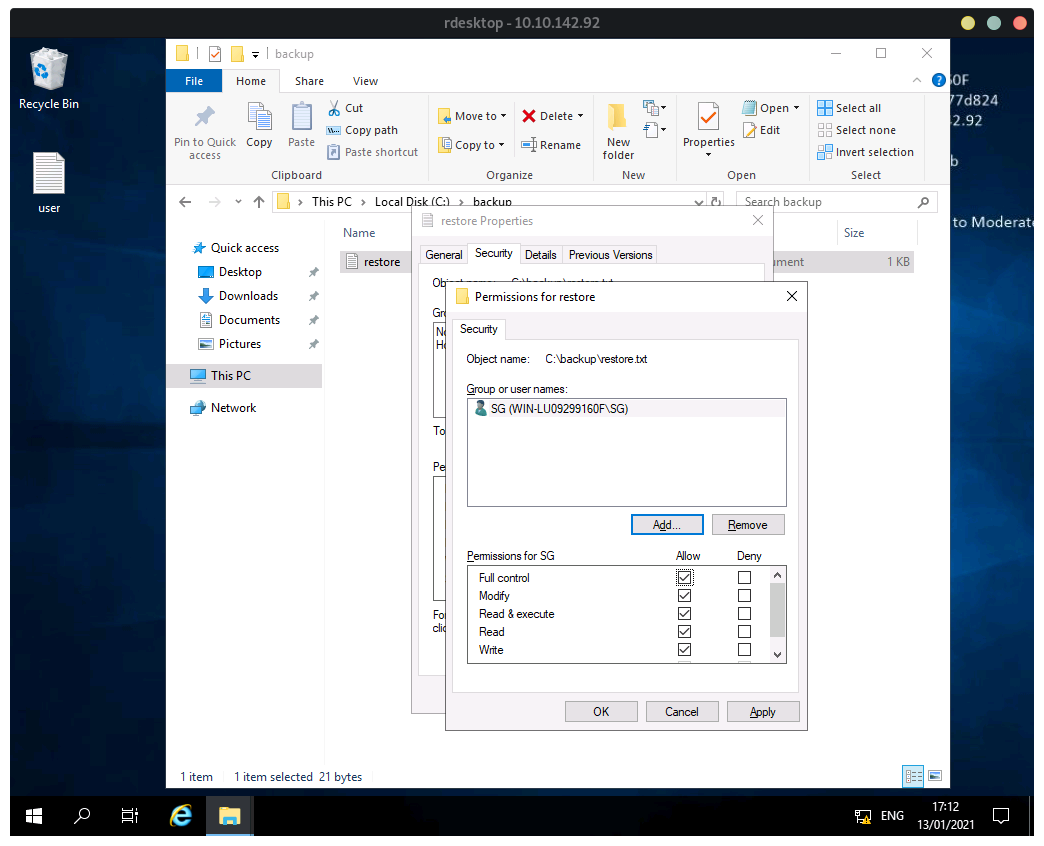
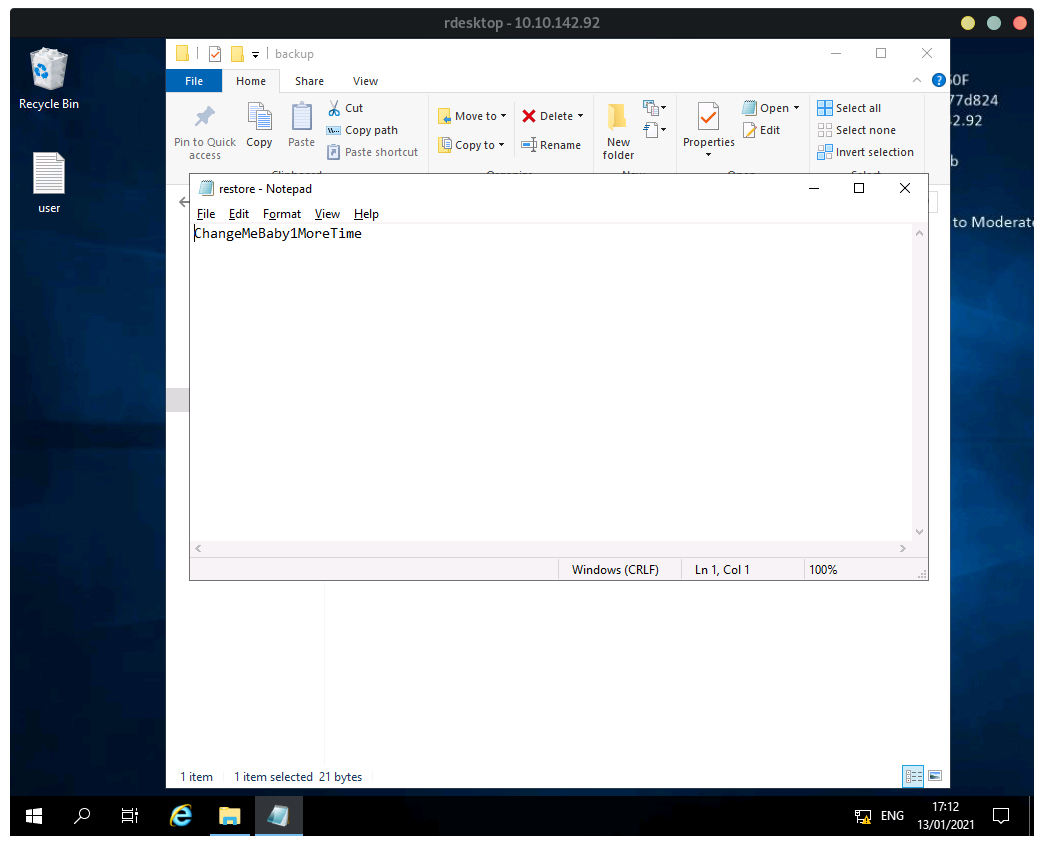
To login as admin click on the Users\Administrator folder, and enter the password in restore.
We can find the root flag on Administrator’s Desktop.
FIN. 🥳