San-Diego CTF 2021: Git Good
May 7-9 (Mostly just the 7th tbh), I competed in the San-Diego CTF, run by ACM Cyber, the cybersecurity club out of UC San Diego. All of the challenges had a element of humour which I enjoyed. I didn’t really do the whole thing but I really enjoyed the challenge git-good so I decided to write it up.
This is a medium web challenge, but I think depending on the CTF it may also be considered easy. Below is the challenge description.
When we go to the website in the description we get the following:
I thought the footer was really funny, because I always scroll to the bottom :)
If we click the Login button in the upper right-hand corner we get the following:
Okay, so now we know we have to look for the login page, or maybe some other page. Since its a CTF (no scanning) then there is probably a robots.txt:
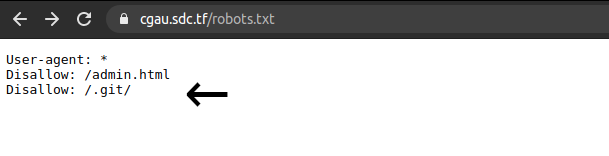
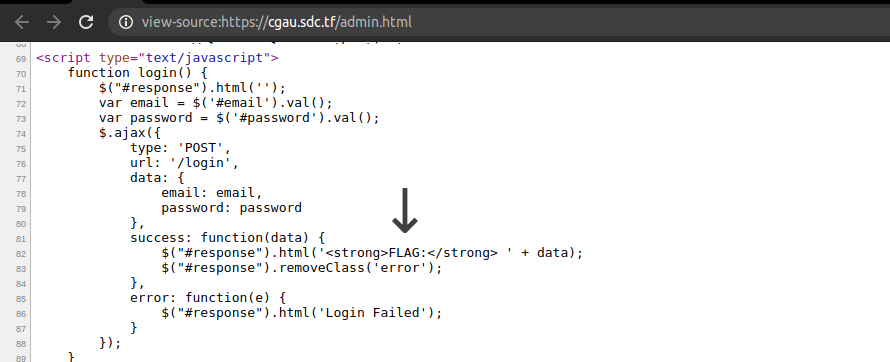
I first saw the admin.html, and checked that out first. In the source code of the admin.html page we find the string “FLAG” and we can see that if we can find correct credentials we can will get the flag.
Since we also know there is a git repo. on the web server, we can clone it using git-dumper (or a similiar tool), and look through the files for credentials and other info.
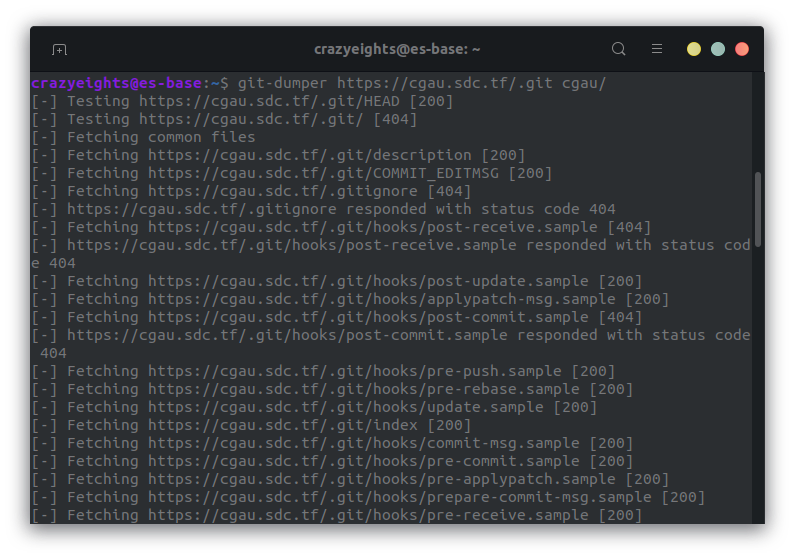
We now have a directory containing the contents of the git repository that was on the webserver.

We find the database users.db, when we open it we find a table of users, and hashed passwords.
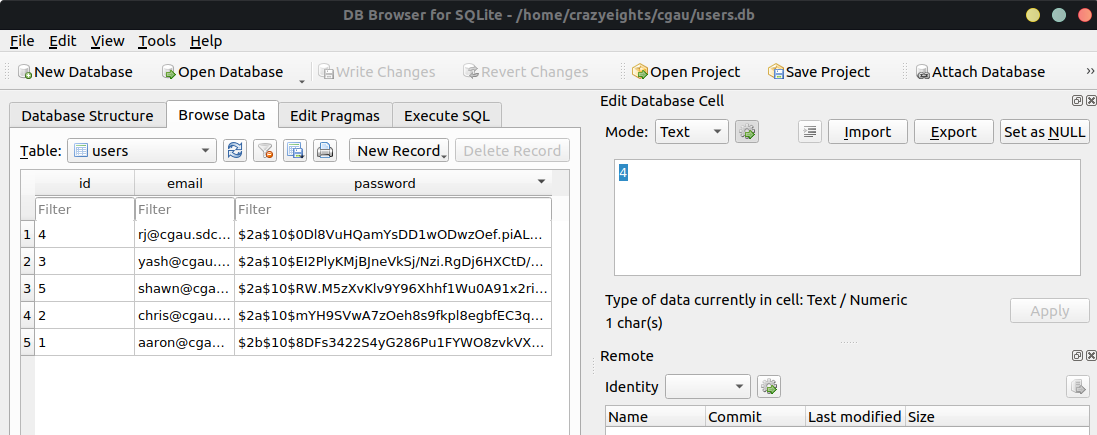
If we look in the source code we can see that when the server recieves a password for a login attempt it uses the md5 algorithm to compute its hash, and takes that hash, and hashes it again using bcrypt.
const password = md5(req.body.password)
...
bcrypt.compare(password, row.password, (err, result) => {
This means there is likely little chance that we can crack the given hashes. But we can still extract other info from the repo.
We can print past commits, and we find that there was a time before the bcrypt algorithm was used in addition to md5:
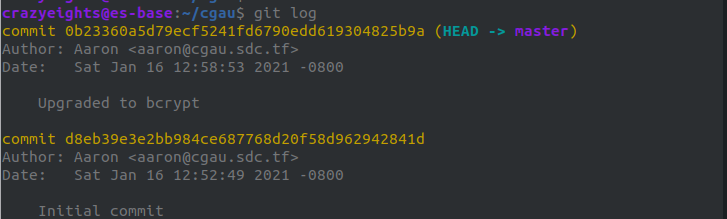
If we can retrieve that info maybe we can crack a users password.
We use the git checkout command to update the files in the working tree to match the version in the commit.
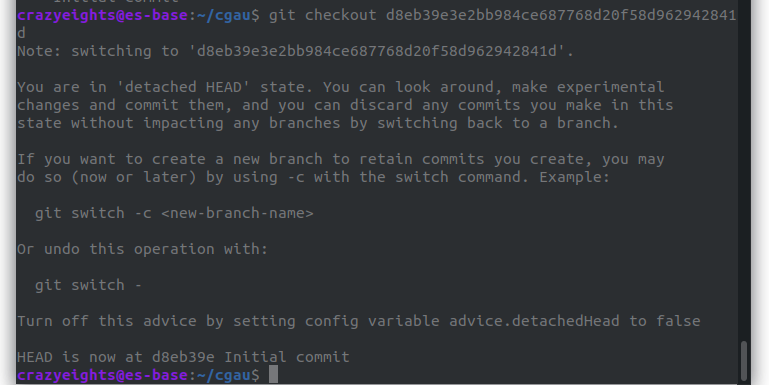
We now have reverted the files to the state they were in at the initial commit.
When we check the users.db file we now the passwords hashed in md5, which will be much easier to crack:
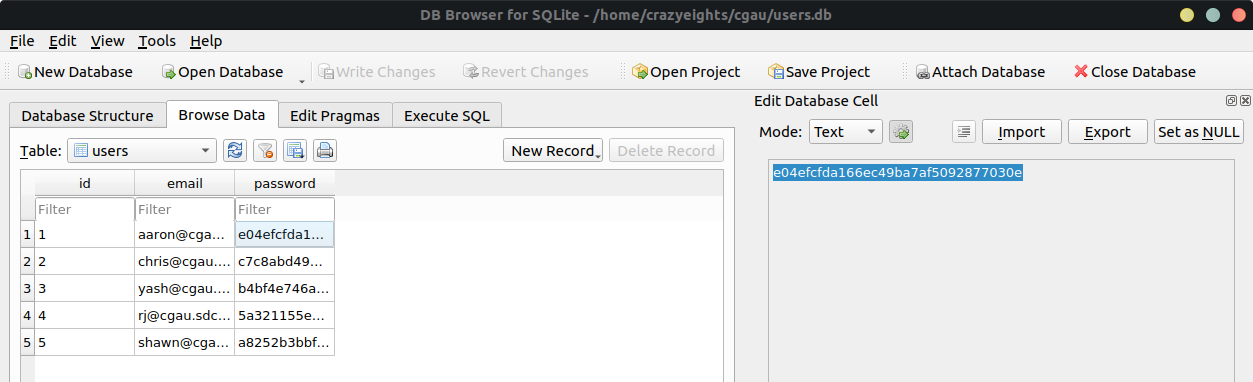
We select the hash for aaron, mostly because he is first in the table. We can google this hash real quick:
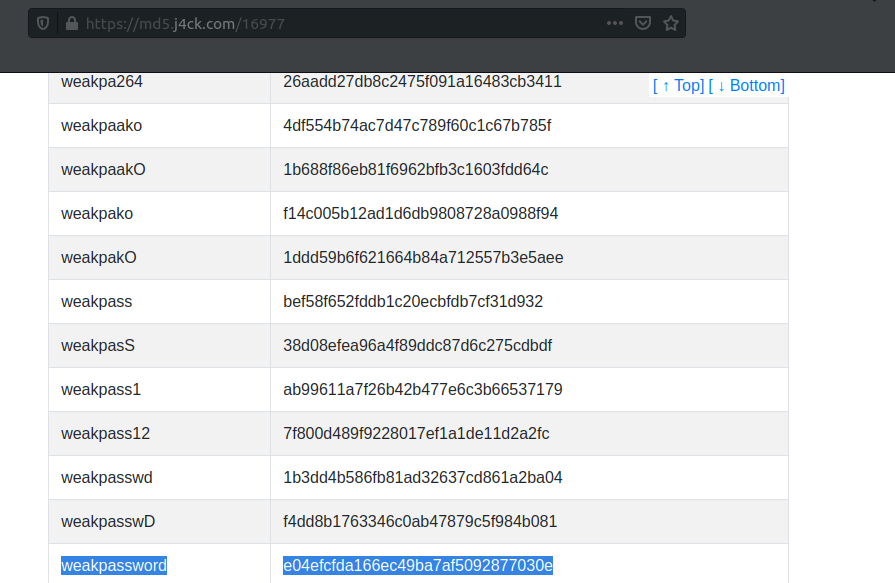
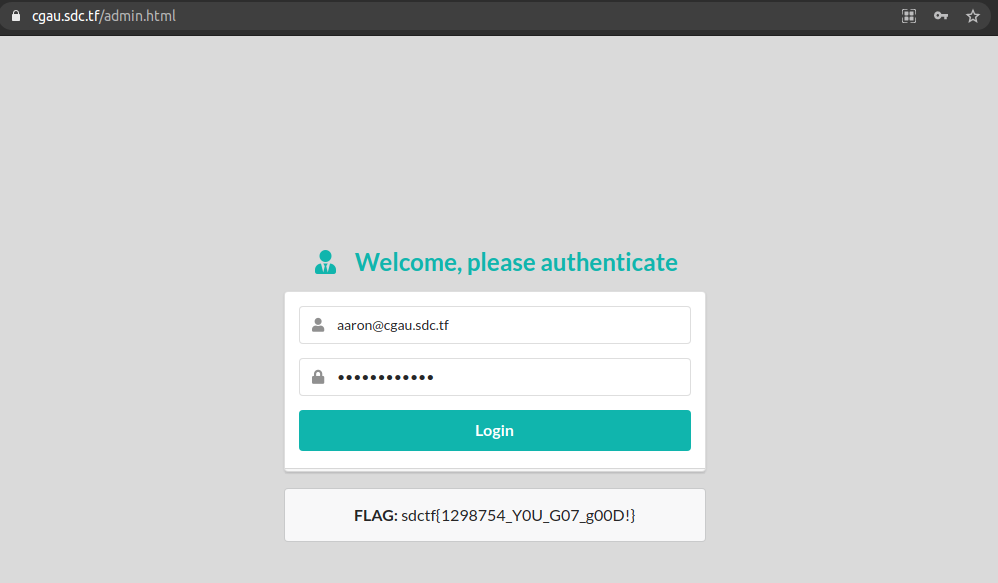
We now have the credentials for the user aaron, we use them to login to the admin.html page and we get the flag:
FIN.