UTCTF 2021
May 12-13th I competed in UTCTF, I decided to write up some of the challenges I thought were cool.
Small P Problems
This was a crypto problem. It was pretty easy, but I suck at crypto so this was the only one I solved from this category.
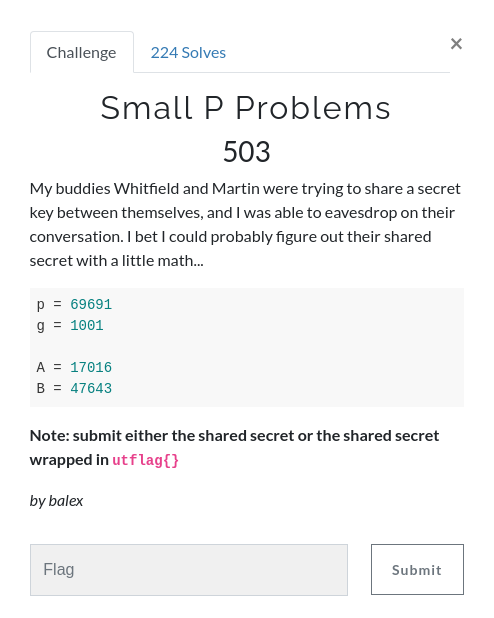
This is a Diffie-Hellman key exchange, we need to find the private keys a, and b:
# The given parameters:
p = 69691
g = 1001
A = 17016
B = 47643
# Calculate the shared key
def diffie_hellman_key_exchange(g, p, a, b):
A = pow(g, a, p)
B = pow(g, b, p)
print("Alice sends: {}".format(A))
print("Bob sends: {}".format(B))
Ka = pow(B, a, p)
Kb = pow(A, b, p)
print("Alice calculates: {}".format(Ka))
print("Bob calculates: {}".format(Kb))
# Find the private key a
for a1 in range(p):
A1 = pow(g, a1, p)
if A1 == A:
a = a1
break
# Find the private key b
for b1 in range(p):
B1 = pow(g, b1, p)
if B1 == B:
b = b1
break
print("Alice - private key a: {}".format(a))
print("Bob - private key b: {}".format(b))
diffie_hellman_key_exchange(g, p, a, b)
The output of the program is:
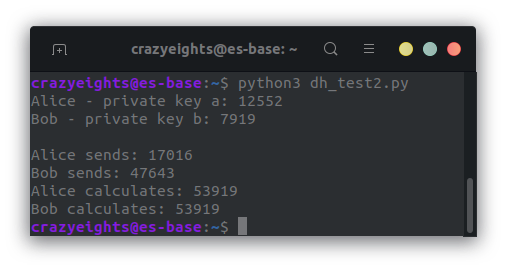
The shared secret is k = 53919. This is also the flag. FIN. 🥳
Hack Bob’s Box:
This was a networking problem. This is the first networking problem I have done, its an awesome category.
Scanning:
In the instructions it says we are only allowed to run nmap on [misc.utctf.live:8121](http://misc.utctf.live:8121) and [misc.utctf.live:8122](http://misc.utctf.live:8122) . Lets do it.
//I shouldn't have done these seperately:
nmap -p 8121 -sV misc.utctf.live
nmap -p 8122 -sV misc.utctf.live
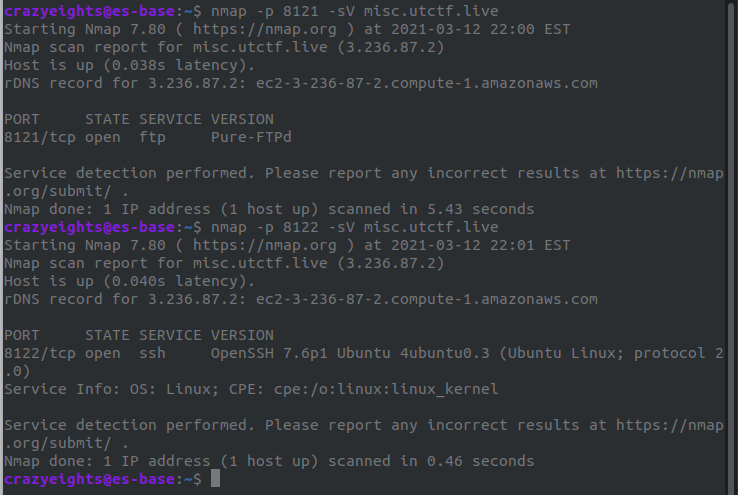
We can see there is FTP, SSH service on these ports.
FTP:
Connect, and login to the ftp server as Anonymous:
ftp misc.utctf.live 8121
I couldn’t actually connect to it for some reason, but they posted the ftp files on the challenge server.
In the firefox folder there is places.sqlite
Open the file places.sqlite:
sqlite> .open places.sqlite
sqlite> .tables
moz_anno_attributes moz_historyvisits moz_meta
moz_annos moz_inputhistory moz_origins
moz_bookmarks moz_items_annos moz_places
moz_bookmarks_deleted moz_keywords
sqlite> select * from moz_places;
In the table moz_places we find a password:
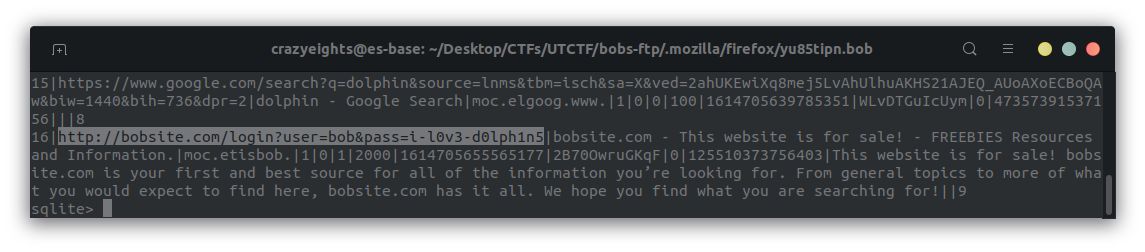
We now have a username, and password: bob:i-l0v3-d0lph1n5 so we can log into SSH
SSH Login:
We login to SSH with the credentials we found, and then use the find command to find the flag.
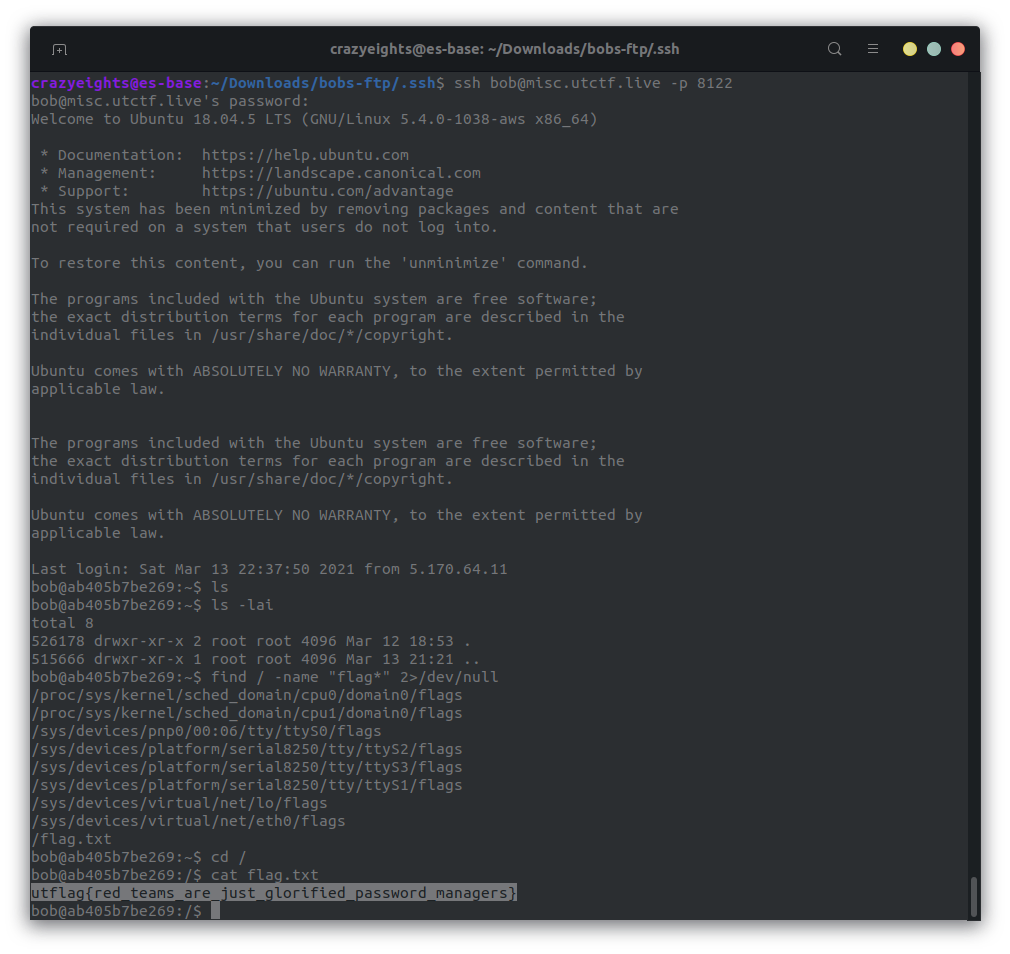
FIN. 🥳
Alright last one. 😐
Sandwiched
Sandwiched was a forensics challenge, I hadn’t done anything like it before, it took some work to solve.
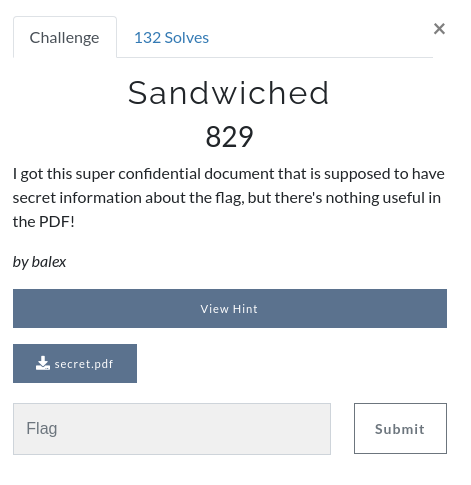
secret.pdf contains the following:
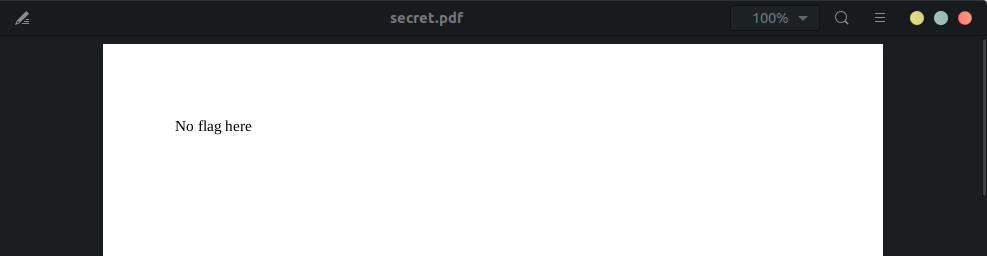
We run foremost on the pdf to extract any files hidden in the pdf:
foremost secret.pdf
We find an image, but it has an unsupported marker type
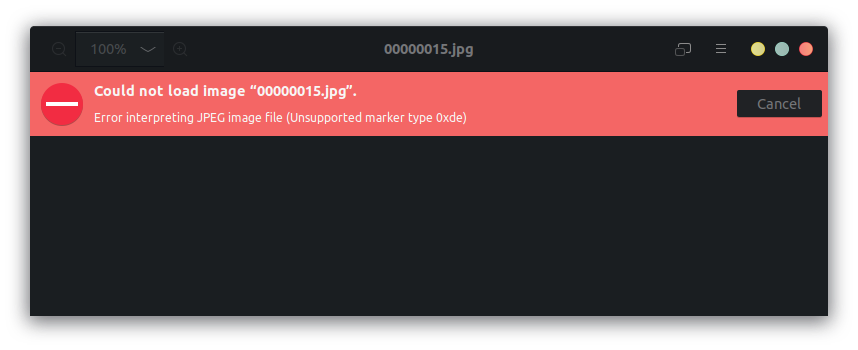
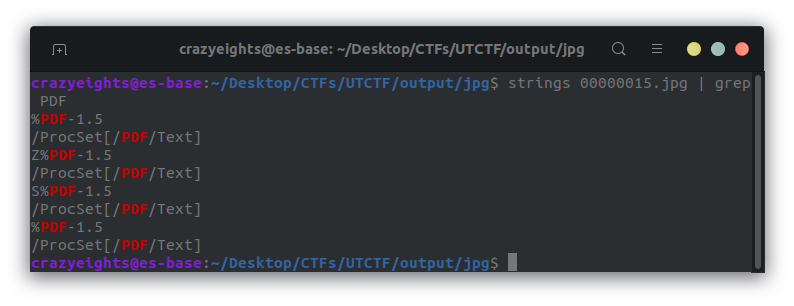
When we open in hexdump we see that there are multiple PDFs inside the image:
If we remove these PDF from the image maybe we can fix the image. I guessed this but it worked 🙂
We write a script to do this.
The PDF start flag is %PDF , which indicates the beginning of a PDF this is 25504446 in hex. The PDF end flag is %%EOF , which indicates the end of a PDF, this is 2525454f46 in hex. We want to filter out everything between the start and end flag for all pdf in the image.
I am sorry for this code.
filtered_hex = ""
eof_flag = "2525454f46" # %%EOF
pdf_flag = "25504446" # %PDF
lpf = len(pdf_flag)
ef = len(eof_flag)
hexdata = ""
start_pdf = False
# Open the image, and read it into a hexstring
with open('00000015.jpg', 'rb') as f:
hexdata = f.read().hex()
i = 0
# loop through the data
while(i<len(hexdata)):
# If we have found a pdf, we want to loop over it and don't write it to the filtered data buffer
if hexdata[i:i+lpf] == pdf_flag:
start_pdf = True
# Write image data into the filtered data buffer if it is not part of a pdf
if start_pdf is False:
filtered_hex += hexdata[i]
# we have reached the end of a pdf
elif start_pdf is True and hexdata[i:i+ef] == eof_flag:
i += ef-1
start_pdf = False
i+=1
#write the filtered data buffer to a new image file
with open("flag1.jpg", "wb") as f:
f.write(bytes.fromhex(filtered_hex))
We run it and we get:
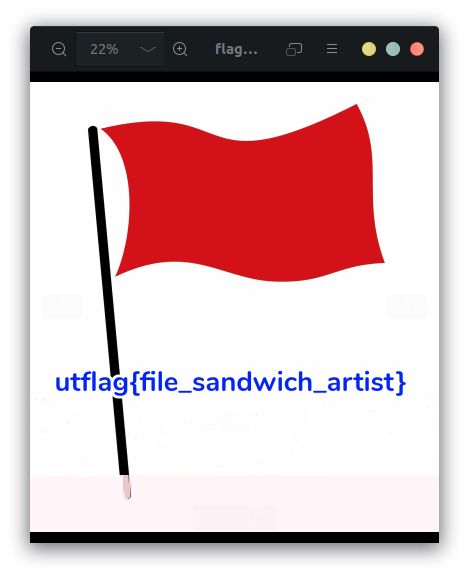
FIN. 🥳
This CTF was fun but I still suck at pwn. 😑